The website is temporarily blocked due to security reasons after a suspicious action was detected. Please email the site owner with the Cloudflare Ray ID and details of the action that triggered the block.

David Bessis wrote a book called Mathematica, arguing that everyone is secretly doing math and can improve their mathematical thinking through practice and self-reflection. He claims that math is a dialogue between reason and instinct, and that it can be a powerful self-help technique for creativity and problem-solving.

This project aims to improve the interpretability of large language models (LLMs) by using sparse autoencoders (SAEs) to untangle superimposed representations into separate, clearly interpretable features. The project provides a full pipeline for capturing training data, training SAEs, analyzing learned features, and verifying results, and it has successfully applied this approach to the ...

HTTP cookies are a small piece of data used for maintaining state on the World Wide Web, but their specification is ambiguous and causes issues with browsers and programming languages. The problem lies in the differing behavior between browsers and languages when handling non-ASCII characters in cookies.

The user investigated why gpt-3.5-turbo-instruct can play chess well while other large language models (LLMs) struggle, and found that recent chat models can also play chess well with the right prompts and examples. The user proposed a theory that OpenAI's base models are good at chess, but the chat interface and instruction tuning used in chat models hinder their performance, and suggested ...

The "Demon Core" is a plutonium core involved in two criticality accidents that killed scientists Louis Slotin and Harry Daghlian, and its story has become a meme with kawaii anime-style drawings and dark humor. The meme's origins and spread are unclear, but it appears to have originated in Japan and has since become a popular internet meme among geeky boys and others who recognize the ...

The author presents novel timing attack concepts that can be used to detect server secrets, including misconfigurations, blind data-structure injection, and hidden routes to forbidden areas, and shares tools and techniques to help automate and improve these attacks. By leveraging timing attacks, researchers can uncover hidden parameters, detect server-side injection vulnerabilities, and ...

The Barning-Hall tree and the Stern-Brocot tree are used to enumerate Pythagorean triples and rational points on a circle, with the Stern-Brocot tree providing a hierarchical ordering of the points by turn angle. The Stern-Brocot tree can be used to compute best approximations of trigonometric functions by stereographically projecting rational numbers onto the circle and using the turn angle ...

Personality basins are mental models that describe how our environment and experiences shape our personalities, and we can change our basins by changing our environment and increasing our learning rate. By understanding personality basins, we can model mental illnesses and develop new approaches to curing them, and we can also use this concept to improve our own lives by trying new things and ...
Please enable JS and disable any ad blocker

The author explores various paintings on Art UK, including rectangular cows, and discovers that cows were a popular subject due to their ubiquity in the British countryside. The author finds that famous artists like Andy Warhol and Franz Marc created cow paintings, but the rectangular shape of cows in some paintings may be due to the emphasis on size and status in the early 1800s.

The author discusses how a large language model can transform a linear narrative into an immersive adventure, citing the example of a game based on their book "The Infernal Machine" that allows players to explore the Soho loft mystery of 1911. The author argues that the key to this capability is the model's increased context window, which enables it to understand and recall complex ...
Multiple state attorneys general signed a document, likely a court filing, with various attorneys listed from Florida, Texas, California, and other states.
The Code Conversion Language (CCL) is a byte-code interpreter in Emacs that can be used for text processing and arithmetic operations, but its I/O facilities and memory access are limited, making it unclear whether it is Turing-complete. Despite some examples of CCL programs being faster than their Emacs Lisp counterparts, the language is hard to debug and maintain, and its use may be ...
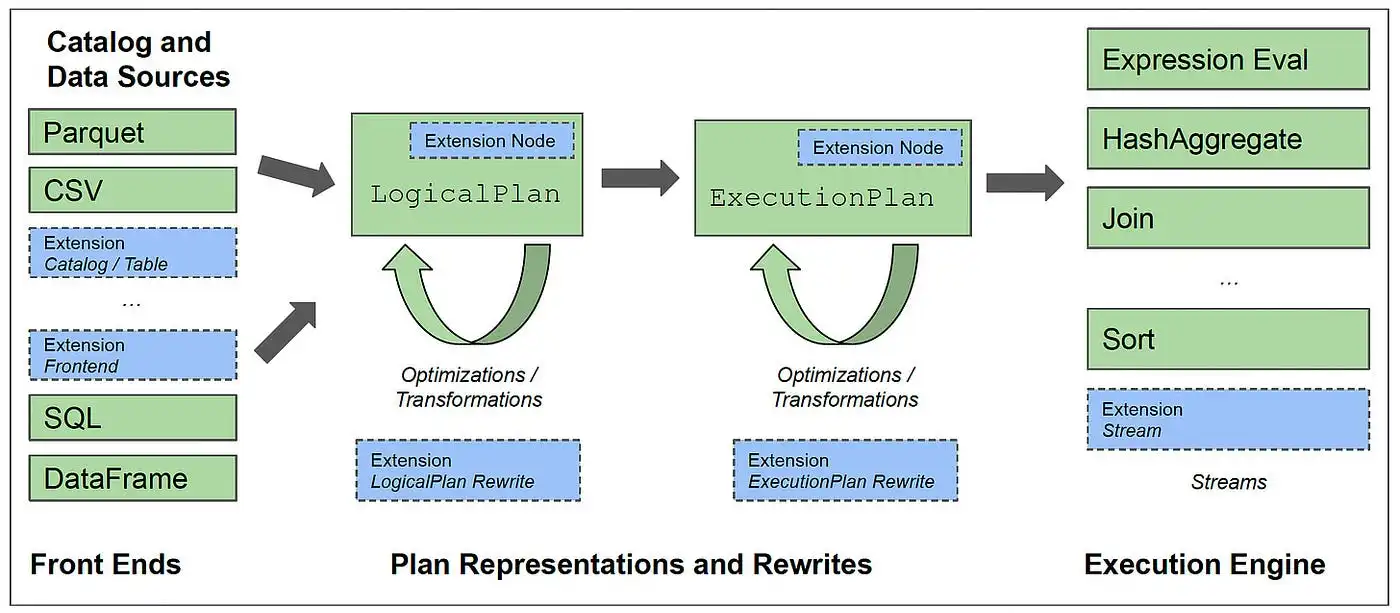
Developers are often conditioned to treat databases as black boxes, but recent trends and projects like Apache DataFusion make it possible for developers to build custom databases and innovate around the developer experience. This tutorial walks through extending DataFusion to add a custom window operator for stream processing applications, demonstrating how to build a custom database and ...
Paul Dirac, a 25-year-old British physicist, developed a groundbreaking theory in 1928 that combined quantum mechanics and special relativity. His equation led to the discovery of antimatter and earned him the 1933 Nobel Prize in Physics.
The author used to manually check units in calculations but now uses the dimensional Haskell package to ensure correctness. The package enforces type-safe dimensions at compile-time.
Arvind and Akhil from Fresco AI are building a tool to help construction superintendents manage documentation with AI. Fresco uses generative AI to create reports and punch lists from short videos or photos taken during site walks.

Hackers breached Andrew Tate's online course, The Real World, revealing 325,000 users' email addresses and exposing the platform's security vulnerabilities. The breach was attributed to "hacktivism" and exposed Tate's platform, which focuses on financial investment and masculinity, to criticism and scrutiny.

The concept of autopoiesis is simulated using a cellular automaton with binary state attribution and a scaling rule, aiming to generate self-rebuilding systems. The simulation involves logic gates, neighbor interactions, and a Φ value that mimics closure, with the goal of achieving autopoietic behavior.
We're sorry, but an unexpected error occurred. Our team has been notified, and we are actively working to resolve the issue.

I got hooked on Qubes OS due to its emphasis on security and privacy, allowing me to compartmentalize tasks and separate contexts with ease. The system's unique offer and tools make it ideal for niche users who value high security, but it requires a specific mindset and discipline to use efficiently.

Spirit Airlines' bankruptcy is not a result of antitrust enforcement but rather poor management and a flawed business strategy. The airline's executives misled the court and shareholders, and the CEO received a $3.8 million bonus before the bankruptcy, highlighting the need for stronger regulation in the airline industry.

Nile is a PostgreSQL re-engineered for multi-tenant applications that provides isolation and flexibility while preserving a single database developer experience. It uses a distributed transaction architecture with a PostgreSQL extension, transaction coordinator, and metadata store to handle DDLs across tenants and physical databases, ensuring robustness and reliability.

Hibernation is a natural state of suspended animation found in various animals, characterized by a controlled reduction in metabolism and physiological processes, and scientists are exploring its potential applications in humans for survival and therapeutic purposes. Despite decades of research, human hibernation remains a mystery, and understanding its relationship with sleep, brain ...

Using refresh tokens with short-lived access tokens simplifies revocation, limits the impact of token leaks, and provides incremental improvements to client security and flexibility in future access grants. However, it also increases client complexity and introduces a single point-of-failure in the authorization server, which can be mitigated with proper design and redundancy.