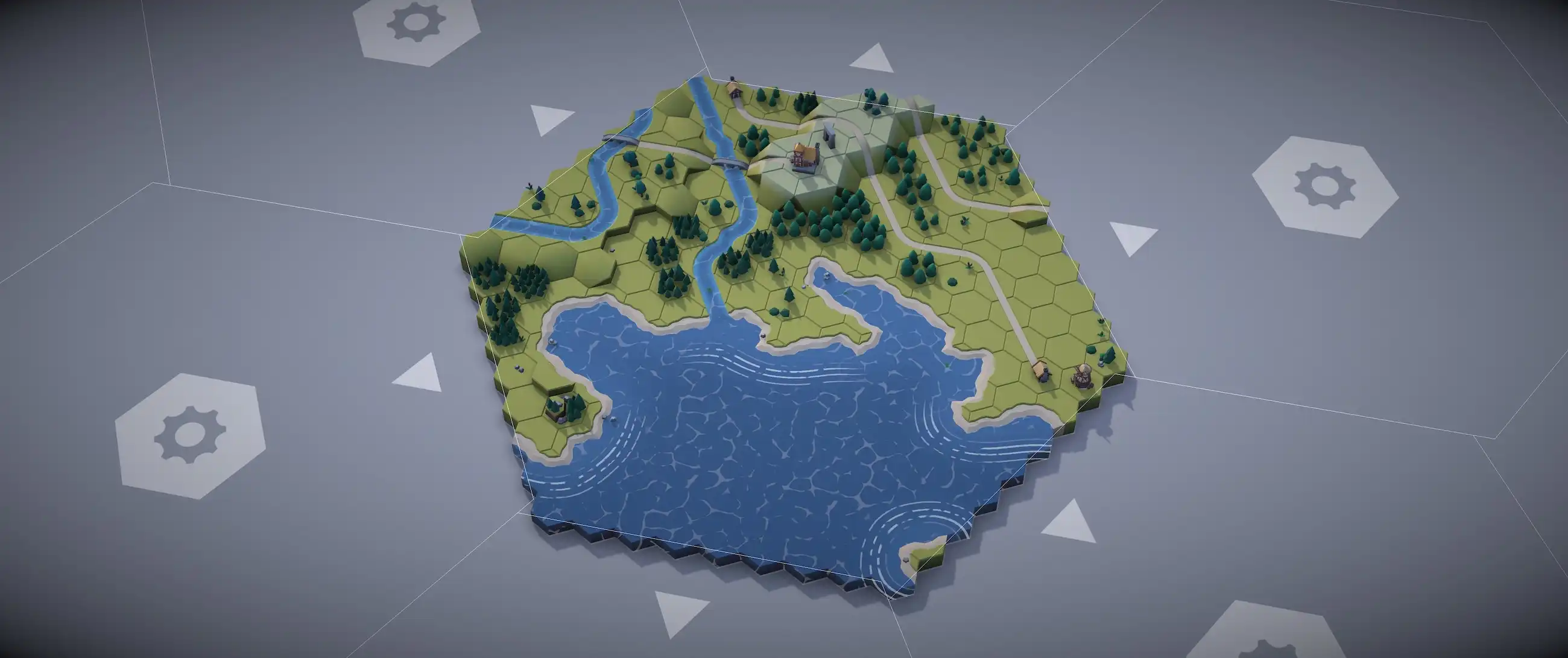
The user built a procedural map generator using Wave Function Collapse (WFC) algorithm, creating a medieval island world with roads, rivers, coastlines, and villages, and overcame challenges such as hex grid geometry and elevation constraints. The generator uses a combination of WFC, Perlin noise, and custom visual effects to create a realistic and immersive environment, and can be interacted ...