Something went wrong, but don’t fret — let’s give it another shot. Some privacy related extensions may cause issues on x.com. Please disable them and try again.
For the best experience, please scan the QR code with your phone's camera to use the app on your mobile device. https://molecheck.info
Please enable JS and disable any ad blocker
I triggered security block likely due to suspicious action, possibly keyword or SQL submission. Please email the owner with details and Cloudflare Ray ID.
People use debuggers for advantages like inspecting state, evaluating expressions and setting breakpoints, but many skip them due to setup difficulties and remote environment limitations. Debuggers offer convenience and power, particularly in standardized IDEs like VSCode and IntelliJ.

To prevent secrets from getting into logs, it's not one silver bullet that solves the problem, but rather a combination of lead bullets that involve understanding data flow, transforming data into safer forms, and using domain primitives. Lead bullets include data architecture, data security fundamentals like minimization and redaction, and tools like taint analysis, domain primitives, and ...
The demo scene, recently proclaimed a UNESCO Living Cultural Heritage, is slowly approaching its demise, as the subculture is dominated by middle-aged individuals and lacks new talent. Its unique essence relies on an unwritten set of rules from the past, making it hard to rejuvenate and preserve its original soul for future generations.
Something went wrong, but don’t fret — let’s give it another shot. Some privacy related extensions may cause issues on x.com. Please disable them and try again.
ISO 8601 formats a date and time including year 2025, week 36, months, and seconds. It allows decimal fractions and optional T symbol with space or underscore alternatives.
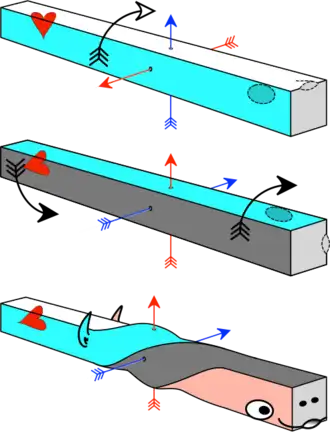
The axial twist theory is a proposed scientific theory that explains unusual aspects of vertebrates' body plans, proposing a rostral head part is turned around the rest of the body with left-handed chirality. This theory competes with Ramón y Cajal's visual map theory and other proposals, but has not gained general recognition.

Sim Wong Hoo founded Creative Technology, developing sound cards such as the Sound Blaster series, while expanding into CD-ROM drives, 3D graphics, and office software. The company faced intense competition, particularly from Aurale and the Vortex card, before ultimately acquiring various companies, including Ensoniq and E-mu Systems.

Bottlefire provides microVMs that are easily built with the open-source CLI tool, bake, and come with networking and directory sharing features. Official images and public images from Docker Hub and GHCR are available for free, with options for higher limits and private image access through paid subscription.
Frederick P Brooks Jr says that software construction has two essential tasks and accidental tasks, most big gains came from removing artificial barriers to accidental tasks, and unless the accidental tasks shrink to near zero software productivity will not gain an order of magnitude.
SQLite is an SQL database engine heavily dependent on TCL for testing, analysis, documentation, and development. It uses TCL extensively in its build process and testing.
Please enable JS and disable any ad blocker
South Korea and the U.S. finalized negotiations to release and return 300 detained South Korean workers from a Hyundai plant raid in Georgia. Seoul expects to send a charter plane and review visa systems for South Koreans on business trips in the U.S.
The tz database is a standardized collection of timezone data and rules used for conversions, and it's distributed as the tzdata package. The database's source files are composed of rules, zones, and links, and can be used to define custom timezones.
Multiple dispatch is an advanced abstraction technique that allows behavior to be chosen dynamically based on the runtime types of multiple objects, and it can be useful when dealing with complex operations involving multiple classes. The article discusses various approaches to implementing multiple dispatch in C++, including the visitor pattern, brute-force if-else checks, and a proposed ...

Researchers found cities operate according to predictable principles like animal biology, challenging the assumption that bigger cities are more sustainable. They discovered a universal scaling law connecting population size to economic activity, CO2 emissions, and transport networks, similar to Kleiber's Law in biology.

The list includes 375 submarine and subsea cable systems across the world, connecting various regions, islands, and countries with high-speed internet and communication capabilities. These cable systems are being deployed to support global connectivity, digitalization, and economic growth in different parts of the world.

The current launcher installs a custom Root CA certificate for Authenticode verification, but doing so makes users liable to having their encrypted communications eavesdropped. Options for remediating the issue include obtaining a legitimate code signing certificate, integrating sigstore, or removing the signature verification functionality altogether.
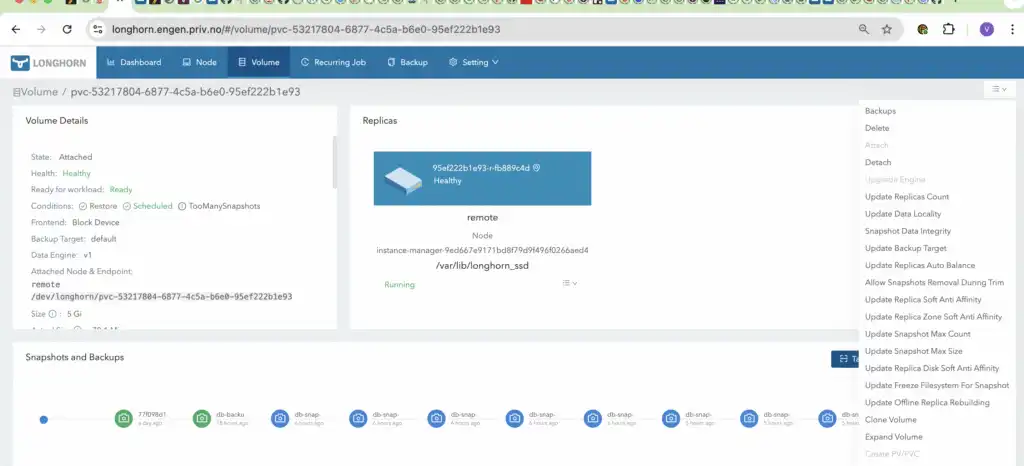
The user has been experimenting with Longhorn, a distributed block storage solution for Kubernetes, and has set up a 2-node cluster with Longhorn provisioned block devices from a pool of SSD and HDD storage. They have also configured backup schedules and replication for their volumes, and plan to use Longhorn as a key component in their disaster recovery strategy.
Please enable JS and disable any ad blocker

The author uses ChatGPT with the GPT-5 model to answer various research-related questions, effectively acting as a "Research Goblin" that provides thorough and accurate information, often in a fun and engaging way. The author finds GPT-5 to be competent, fast, and useful in daily research and development, often surpassing manual searches and allowing for more time for other activities.
Here is a 2 sentence summary of your input in 200 characters or less.
Researchers propose a composite design pattern that combines functional and object-oriented programming to facilitate both tool extension and data extension without code modification. This new approach resolves the tension between the two design strategies and suggests new linguistic facilities for languages with class systems.
The user wants PKM apps to automatically resurface relevant information based on their current context, allowing them to re-engage with existing data and reduce information overload. They propose features like "This Day in History" sections and custom views to help users prune stale data, reduce choice paralysis, and create serendipity.
You're looking for DIY animatronic Halloween display resources that fit a tight budget. You can try Instructables and YouTube tutorials as they offer step-by-step guides and troubleshooting tips suitable for kids with some tech experience like Arduino or Raspberry Pi projects.

Craig Underwood's California farm and David Tran's Huy Fong Foods broke their 28-year partnership over a disputed payment, causing a global sriracha shortage and leaving both businesses financially struggling. Seven years later, Huy Fong has been surpassed by Tabasco as the top-selling sriracha brand, and both Underwood and Tran remain bitter about the partnership's collapse.

Kate Bridget Li, a Palo Alto RV landlord, charges low rent and donates most to her ministry, while city officials debate banning "vanlording" for oversized vehicles. Li sees her mission as helping the less fortunate, but some residents view her as a wealthy person exploiting the city's vulnerable residents.

The lakeFS team built a native Iceberg REST Catalog by leveraging lakeFS's versioning engine and transactional guarantees to create a two-layer pointer architecture, allowing for seamless integration with existing data workflows. This design process, which included rigorous upfront planning and iterative refinement, enabled the team to anticipate and solve complex challenges, ultimately ...