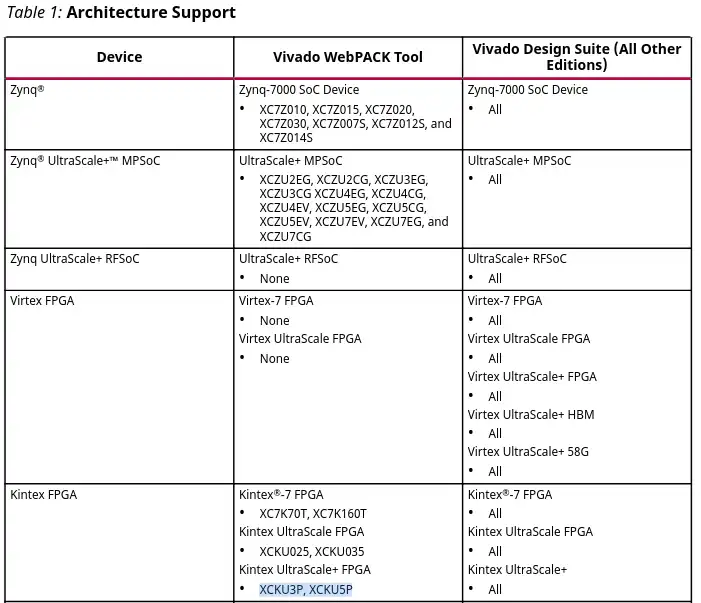
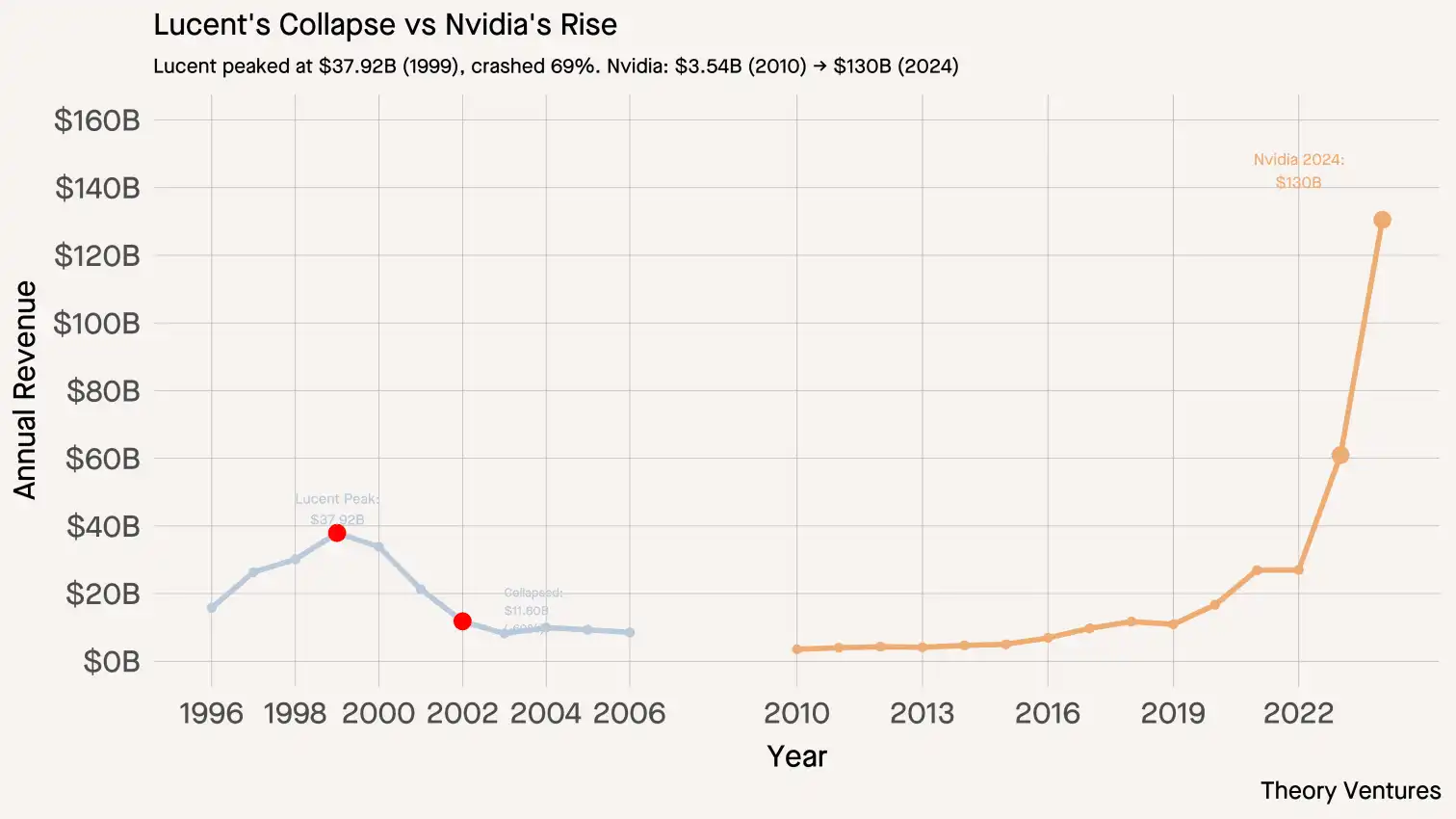
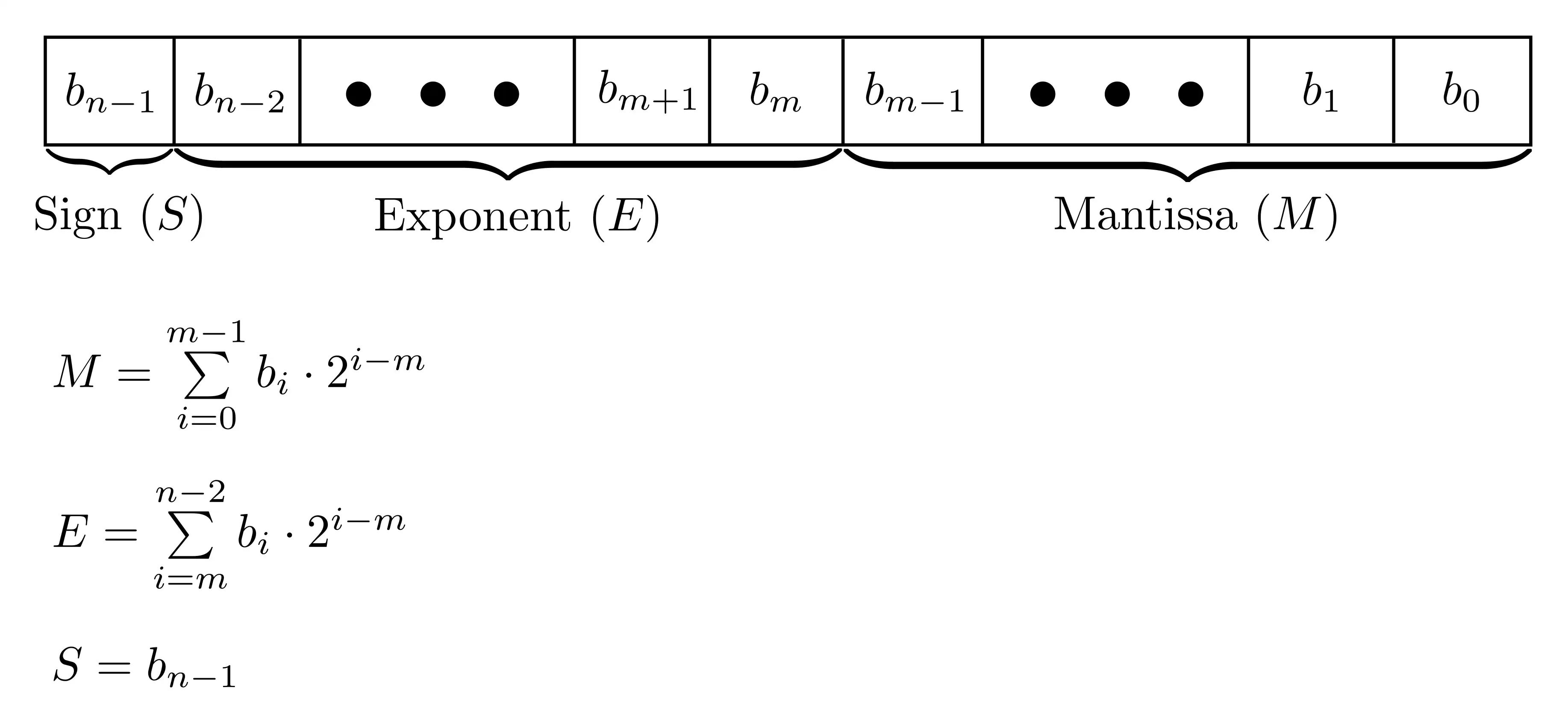
A user created a map showing relationships between VPN companies, media companies, and affiliate programs, highlighting corporate ownership, paid relationships, and partnerships. The map reveals a complex web of connections between VPN companies, including ExpressVPN, NordVPN, and Surfshark, and their affiliate programs.