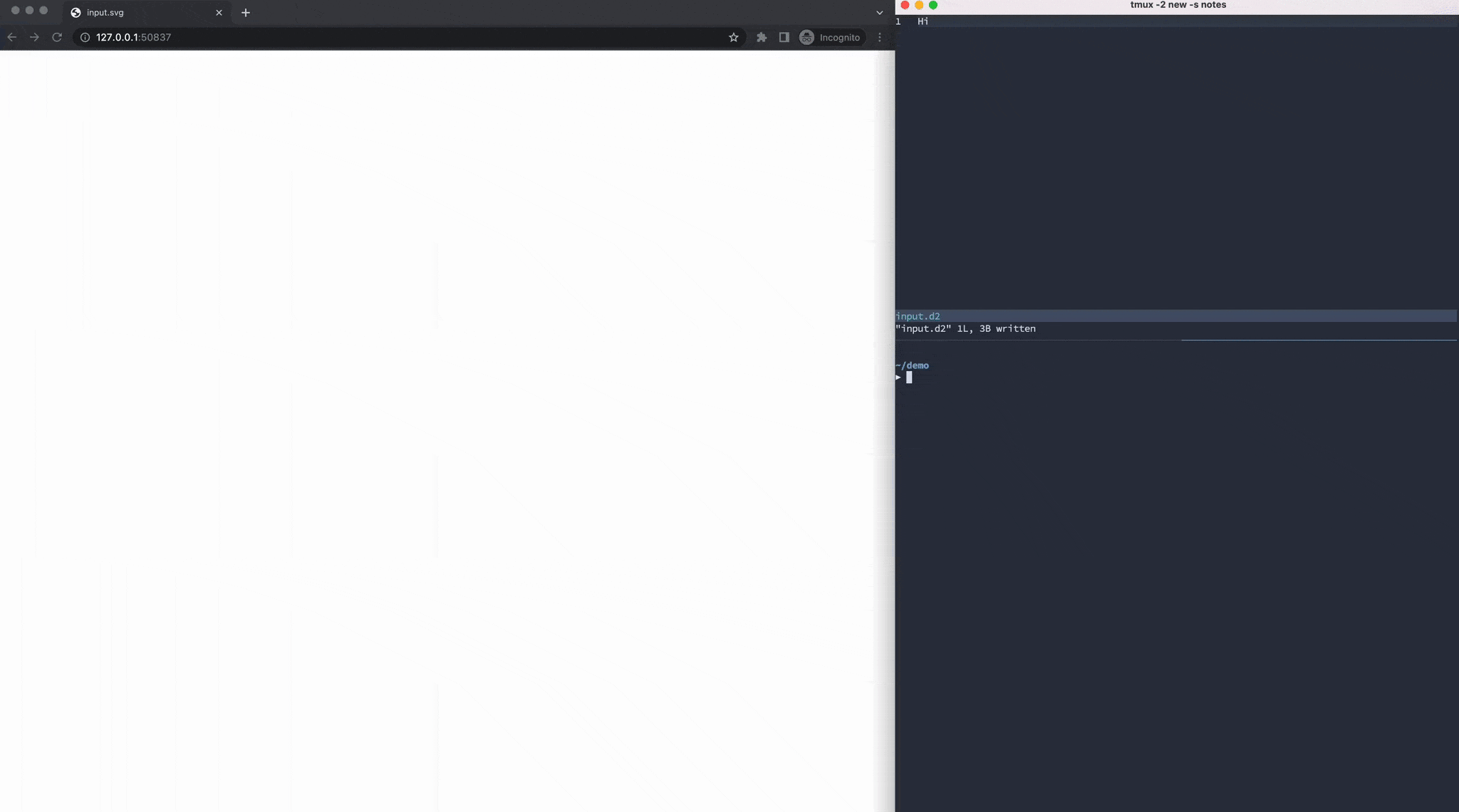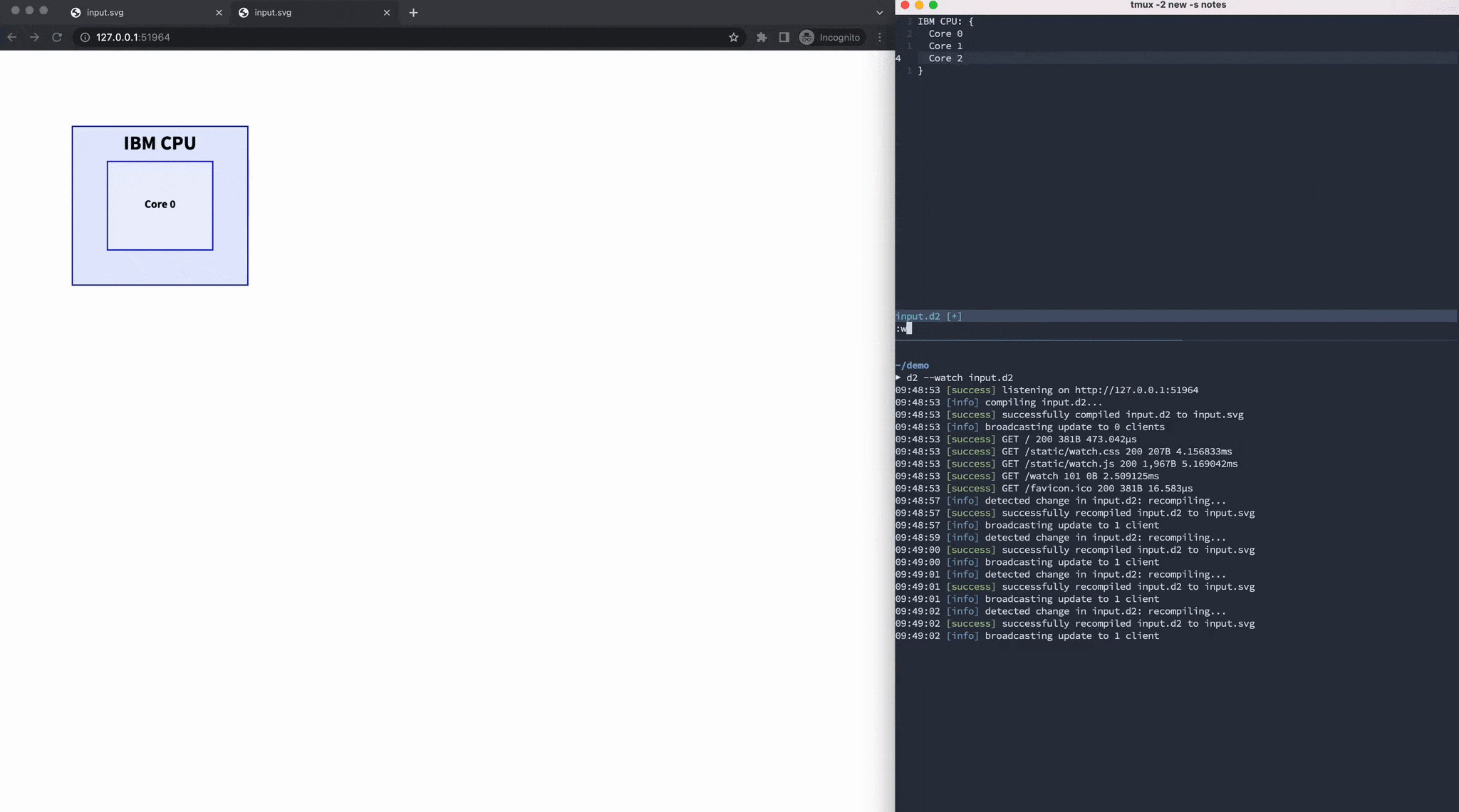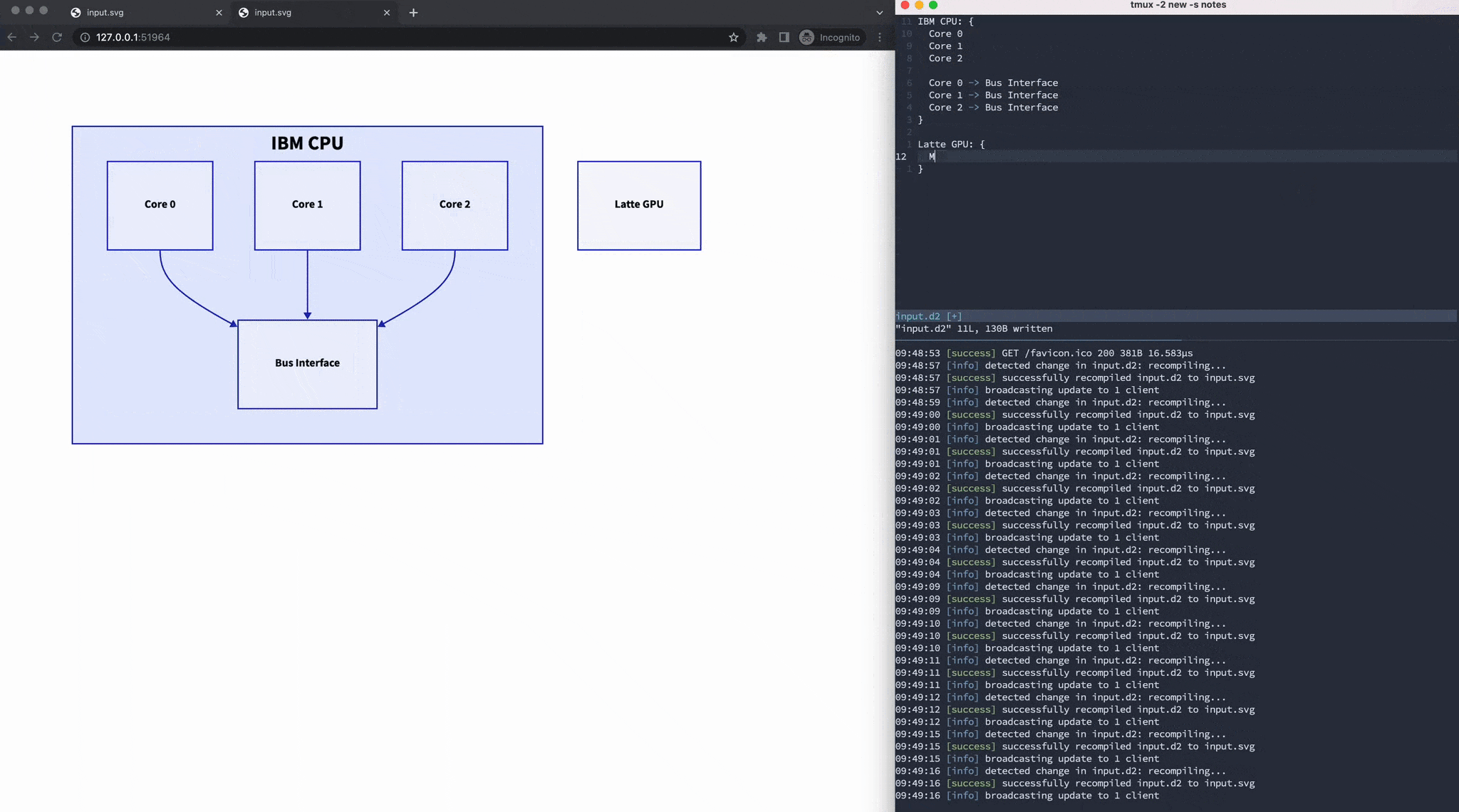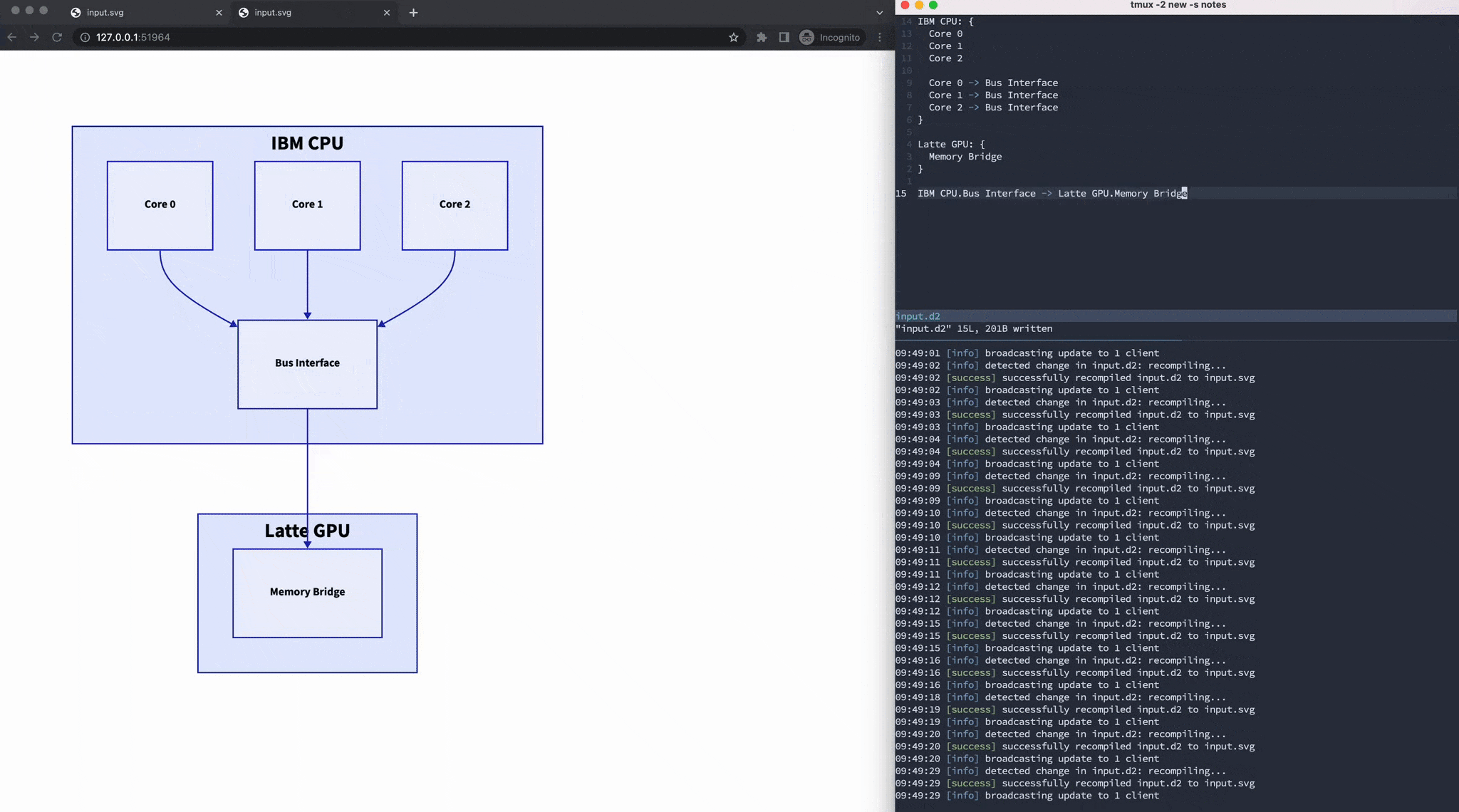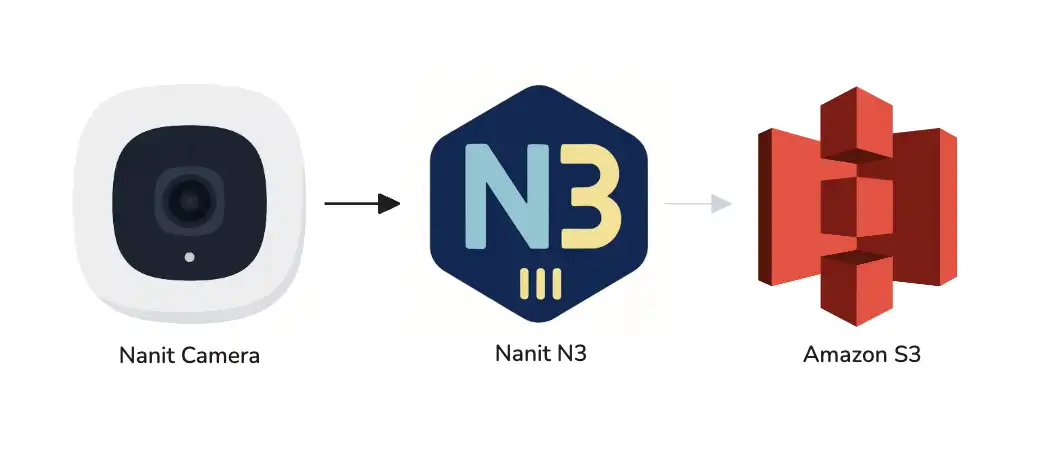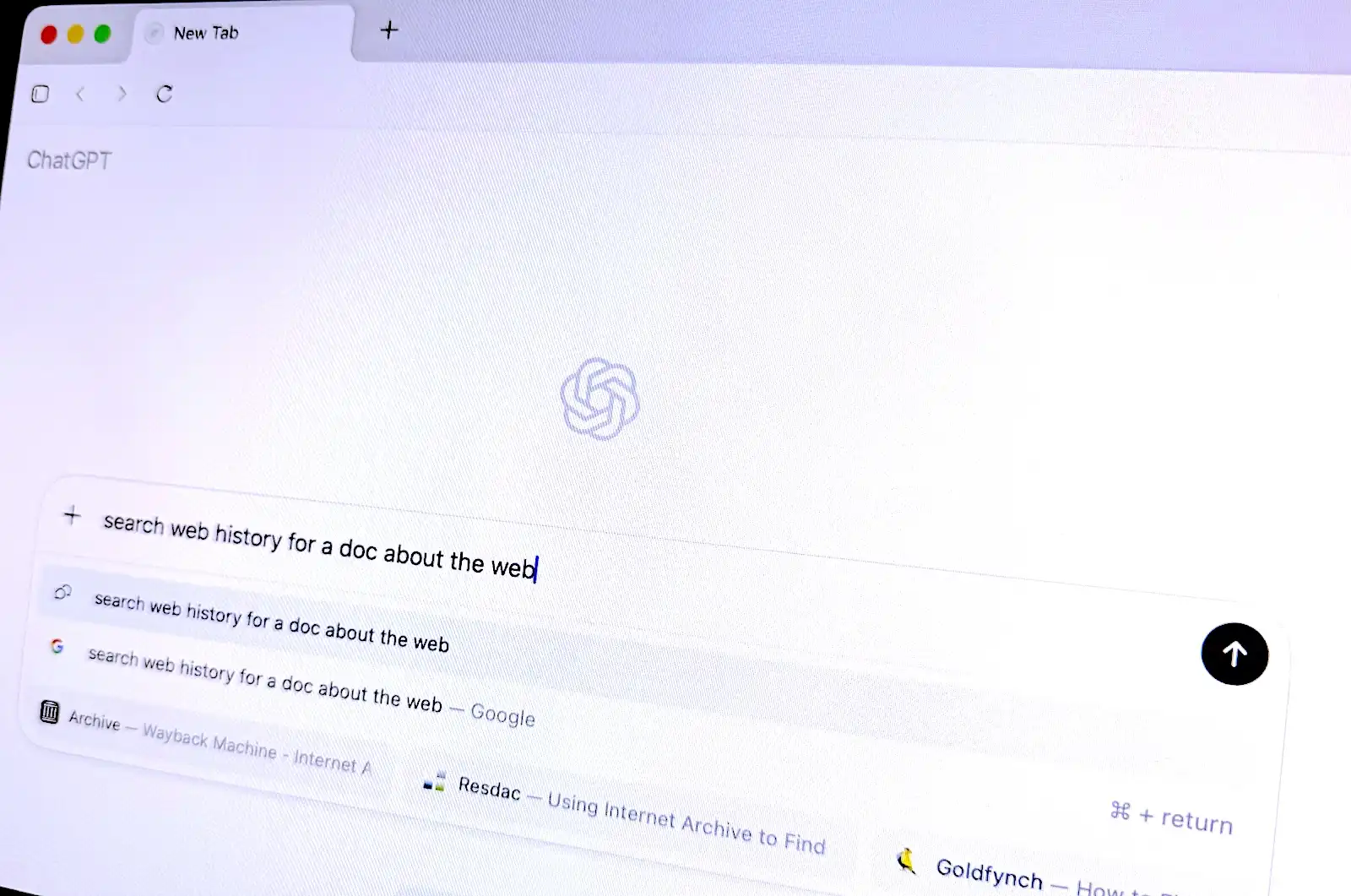
OpenAI's new browser Atlas is an "anti-web" browser that actively fights against the web by substituting AI-generated content and encouraging users to navigate through unreliable results. The browser's "agent" functionality allows OpenAI to gather vast amounts of user data without consent, raising concerns about surveillance and the dismantling of the web's original design.