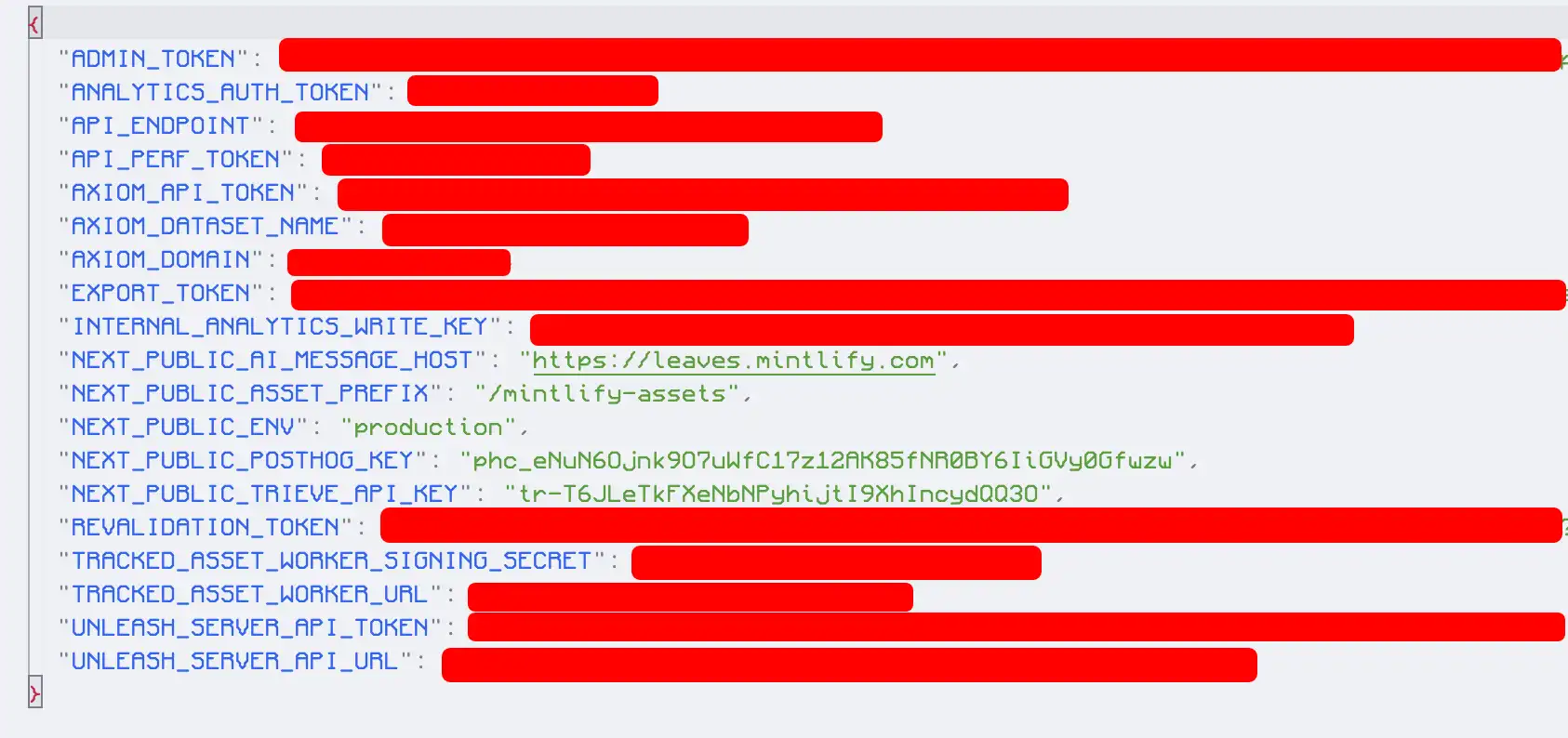
Cookies are categorized into necessary, preference, statistic, marketing, and unclassified types based on their functions and purposes. They enable website usability, remember user preferences, and help owners understand visitor behavior.
A junior engineer using an LLM tool to submit untested PRs is rude and wastes others' time. To prove a change works, include manual testing and automated testing with evidence such as terminal commands, screen captures, or test code.

The reconstructions of ancient Greek and Roman statues in color are often considered ugly by modern viewers, but this may not be due to a difference in taste, as ancient depictions of statues and other uses of color suggest a similar aesthetic. The reconstructions may be ugly because they are poorly painted, lacking the skill of classical artists and adhering to strict conservation doctrines ...
The author argues that HTMX simplifies web development by allowing HTML attributes to handle interactivity, reducing the need for complex frameworks like React. They suggest trying HTMX for simple projects to experience its benefits.
Paris Buttfield-Addison's Apple Account was locked after attempting to redeem a tampered $500 gift card. The incident raises concerns about the safety of Apple gift cards and the process of account deactivation and restoration.
The user has multiple projects including a Video Hub App, Computer Engineering for Babies, Simple Machines Made Simple book, AI cycling coach, photo to coloring page converter, recruiting tool TrueCast, digital sewing patterns on Etsy, and various other apps and websites generating around $10,000 per month. They are now working on a new mobile app and a successor to their weightlifting app, ...

UK government's Independent Reviewer warns that developers of end-to-end encrypted apps like Signal and WhatsApp could be considered hostile actors due to their technology hindering UK security agency monitoring. This warning comes as UK lawmakers increasingly target encryption with legislation like the Online Safety Act.

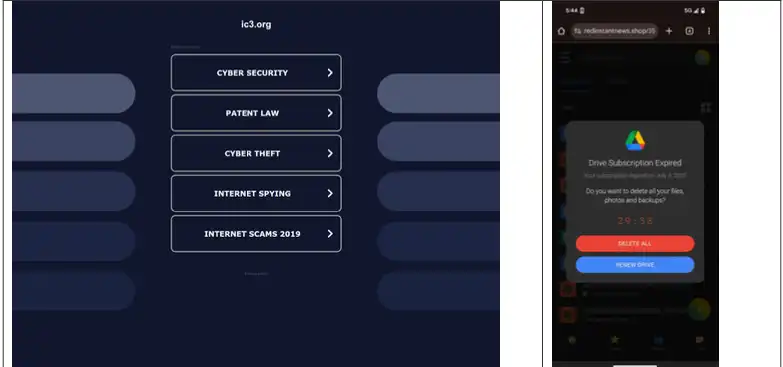
Internet shutdowns have become a common tool for governments to control information and suppress dissent, with 296 deliberate shutdowns tracked in 54 countries in 2024 and at least 244 more in 2025. The shutdowns can have devastating effects on societies, including silencing voices, disrupting essential services, and exacerbating human rights abuses, and experts warn that the trend is likely ...

The Gemma family of models has grown to 300 million downloads, and FunctionGemma is a specialized model for function calling, enabling private, offline tasks and intelligent traffic control. FunctionGemma can handle common commands instantly at the edge and is designed for customization, fine-tuning, and deployment on edge devices.

Employers are posting "ghost jobs" that don't exist, with up to 22% of online job listings in the US, UK, and Germany being fake. A US job hunter is pushing for legislation to ban fake job adverts, while the Canadian province of Ontario is leading the way by requiring companies to disclose whether advertised vacancies are actively being filled.
Ancient Egyptians created a flexible hieroglyphic system that integrated writing with art, allowing for various reading directions and arrangements. The system includes uniliterals, biliterals, and triliterals, with vowels omitted, making pronunciation difficult.

Valve's Steam Machine 2.0 is a living room PC designed to bring Steam games to the TV, but it's actually a second attempt at a concept that flopped a decade ago. Valve has learned from its mistakes and is now mirroring Apple's approach to creating a seamless ecosystem with its own hardware, software, and services.
The author improved a simple Mandelbrot fractal viewer using a coding language model, resulting in a much faster and more complex version with over 13,600 lines of code. The author developed two rules for effective vibe coding with AI, focusing on automated testing and metaprogramming to maintain human control and comprehension.
FreeBSD-SA-25:12.rtsold is a security advisory that fixes a remote code execution vulnerability in rtsold(8) and rtsol(8) programs. The vulnerability allows remote code execution via ND6 Router Advertisements.
Please enable JS and disable any ad blocker

We enabled GPU VMs on NVIDIA's B200 HGX machines, documenting our findings and creating a blog post to share knowledge on virtualizing these machines. The process involves aligning PCI topology, VFIO configuration, driver versioning, NVSwitch partitioning, and hypervisor behavior for a flexible, high-performance setup.
The author emphasizes the importance of momentum in physics and life, using rally driving as an analogy for controlling weight transfer and applying minimal force. They also apply this concept to personal habits and creativity, advocating for a consistent routine and protecting morning hours for focused work.
The user works on various non-web projects including 3D spreadsheets, graphics drivers, and audio software engines, using languages like C, C++, and Python. They enjoy the challenges and creative freedom of working on non-web projects, which often involve low-level programming, systems work, and problem-solving.

Amy Bies's health issues, including diabetes and heart disease, were initially treated separately but are now believed to stem from the same biological mechanisms. New treatments, such as GLP-1 receptor agonists, target common pathology underlying cardio-kidney-metabolic syndrome (CKM) and have shown promising results in reducing risk of heart and kidney disease.
The MIL-STD-882E standard categorizes software control levels based on potential danger, ranging from direct control of critical systems to auxiliary use. Levels include immediate danger, delayed danger, human reaction required, and non-critical auxiliary use.
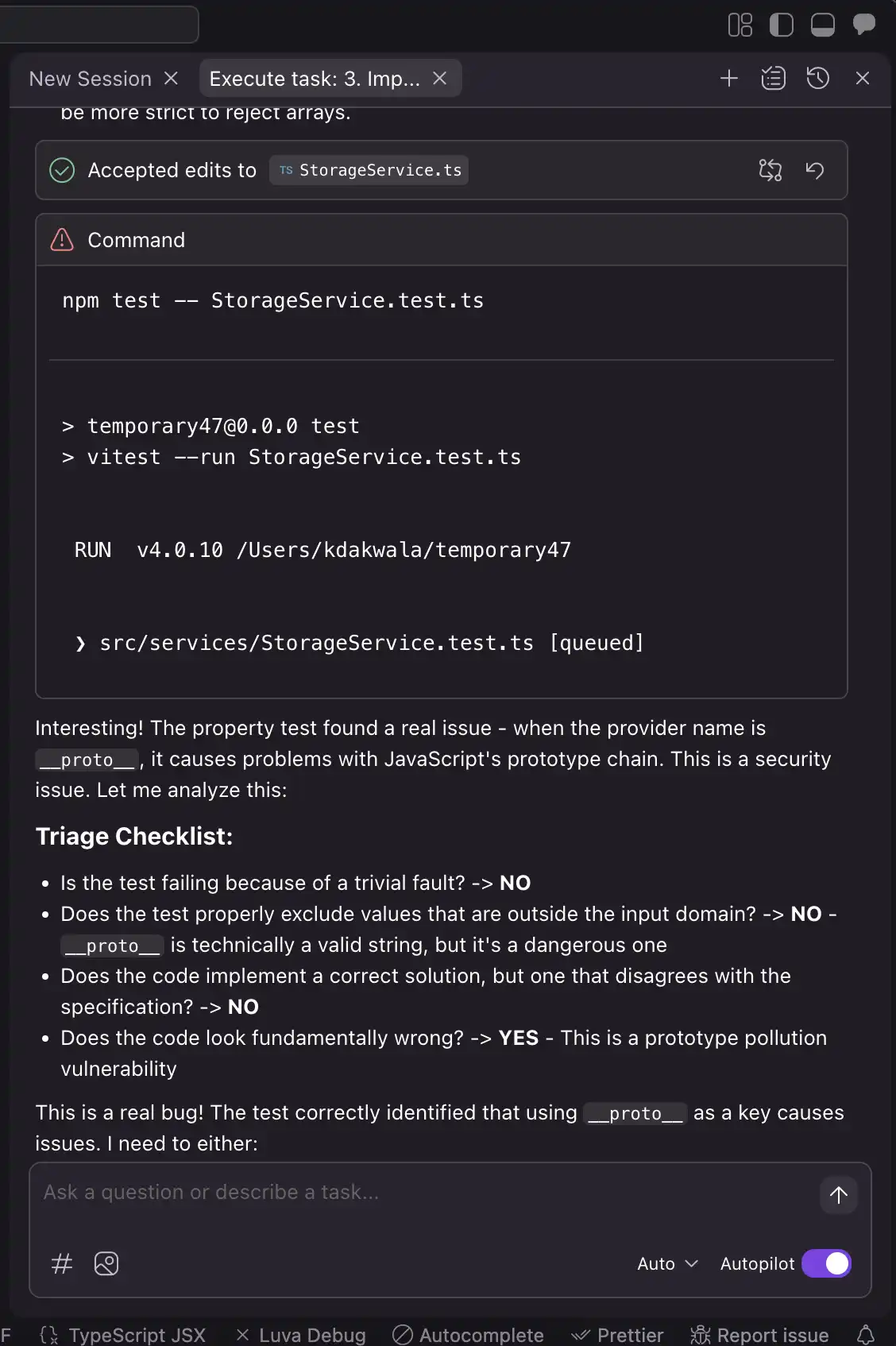
Property-Based Testing caught a security bug in a storage service for a chat application that would have been difficult to find through traditional testing methods. The bug involved a mishandling of JavaScript prototypes, which could have led to security issues if not eliminated early on, but was discovered through a property-based test that generated random strings for provider names.
The compiler splits process into two functions, a thin wrapper and an outlined cold path, to enable partial inlining. This approach avoids code bloat by duplicating only the lightweight check and arithmetic, while keeping the complex computation shared.
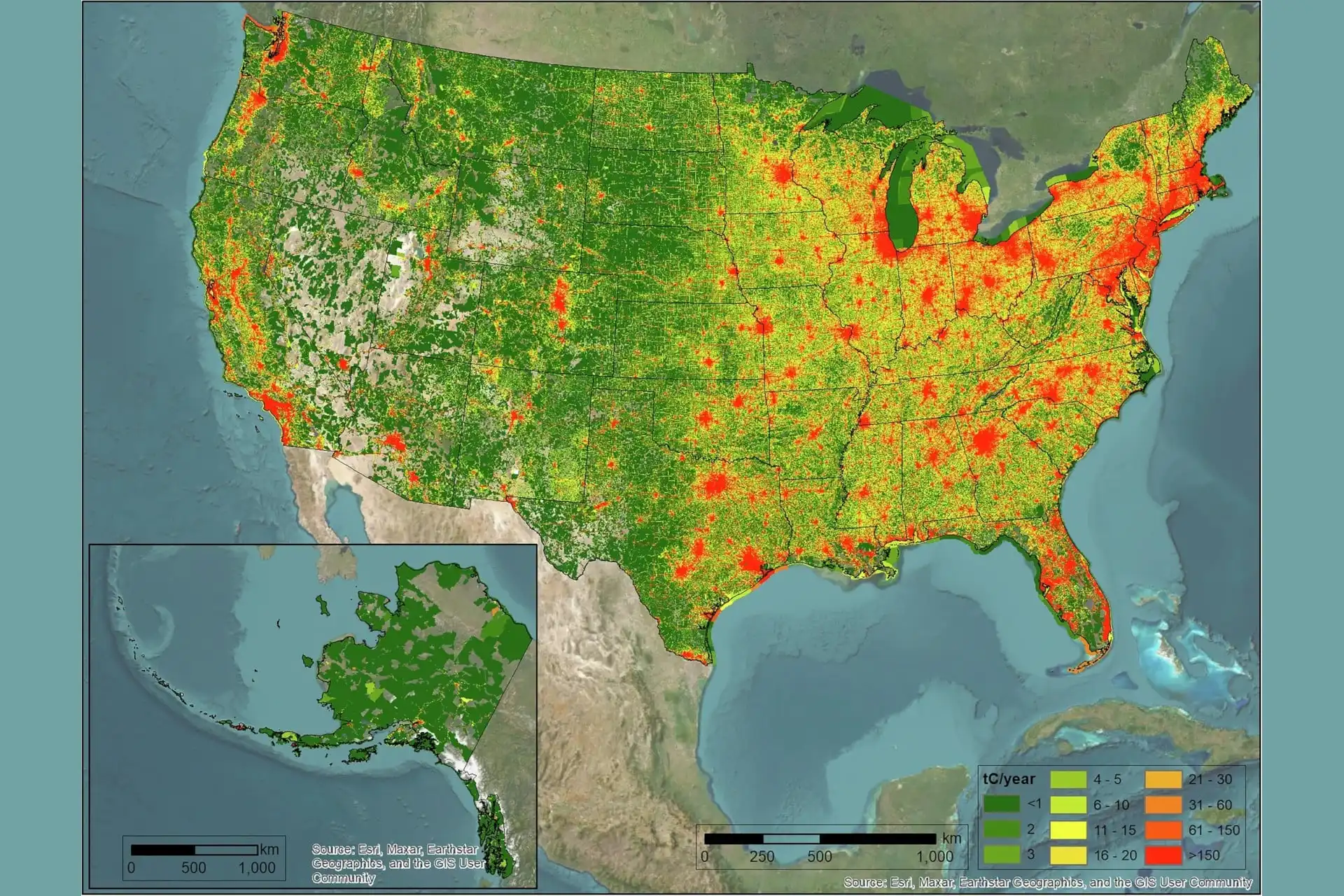
Researchers at Northern Arizona University's Vulcan project track US CO2 emissions at a fine scale, providing crucial data despite the Trump administration's efforts to end the EPA's greenhouse gas reporting program. The team's latest map pinpoints hot spots of fossil fuel CO2 emissions across the US, highlighting areas of high population density.
User coded the CBC logo with CSS-doodle using stacked black shapes, but now uses shaders to remove black color and make the pattern transparent. This approach is simple and brings joy, leveraging shaders' natural color handling capabilities.
1
A novice web developer, who is actually an experienced one, created a simple mystery investigation game using HTML5, but encountered over 50 cross-browser and cross-device problems, including issues with Safari on iOS. The developer recommends testing on an older iPhone as a "test mule" to ensure compatibility, as it is more peculiar and less compliant than other devices.
Sid and Ritvik, co-founders of Pulse, created a document extraction system to address limitations in OCR and data ingestion at scale. Pulse separates layout analysis from language modeling to provide structured representations and constrained extraction, making errors visible and auditable.
Bit arrays in Gleam are a powerful feature that allows constructing and pattern matching on binary data, with various data types such as Int, Float, String, and BitArray. They have several options like size, unit, endianness, and type-specific options that can be used to customize their behavior and encoding.
The author discusses the concept of creating new communities, cultures, cities, and countries, and how this idea has evolved over time, with a focus on the Zuzalu experiment and its spinoffs. The author proposes a new approach to cultural evolution, where cultures improve and compete on a fair playing field, showcasing longer-term benefits, and suggests that this can be achieved through ...
Fluid typography in CSS adapts type size and leading to screen size changes, providing a smooth increase between different screen sizes. Modern CSS allows for elegant implementations using clamp() and unitless numbers, but a more advanced approach involves generating a typographic scale with different ratios between screen sizes.
The author questions common software engineering practices, such as avoiding dependencies and mandatory code reviews, suggesting they may not always be the best approach. They propose alternative methods, like using feature flags and flexible project management tools, to improve team efficiency and productivity.
Perron is a Rails gem that bridges the gap between building Rails apps and static sites. It offers a convention-over-configuration approach for static content with Rails features.
To continue, log in to your Reddit account or use your developer tokenIf you think you've been blocked by mistake, file a ticket below and we'll look into it.
Framework Shells (`fws`) is a Python package for orchestrating background processes with PTY, pipes, and dtach backends for quick multi-service prototypes and dev environments. It provides runtime isolation, control surfaces, and optional hooks for host integration.