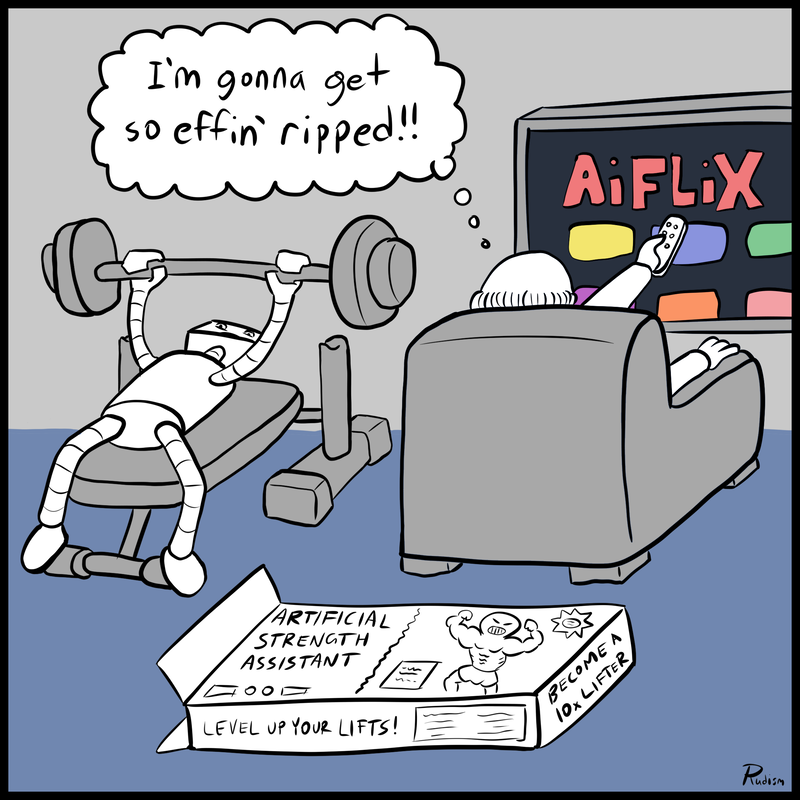
Grid Lanes is a new CSS feature that allows for flexible masonry layouts on the web, using grid-template-columns and grid-auto-flow to create a layout that works on all screen sizes. It also introduces a new concept called "tolerance" that lets developers adjust how picky the layout algorithm is when deciding where to place items.
Sorry to interrupt
A digital museum of video game levels

2025 was a transformative year for LLMs with the emergence of Reinforcement Learning from Verifiable Rewards (RLVR) and the development of new LLM apps and agents. The industry is on the cusp of significant progress with LLMs displaying jagged capabilities, empowering regular people to approach programming, and opening up new possibilities for software development and interaction.

The author reverse engineered a TP-Link Tapo C200 camera's firmware using AI and found several security vulnerabilities, including a private key exposure and integer overflows in the HTTPS server and ONVIF service. The vulnerabilities allow for MitM attacks, remote code execution, and enumeration of nearby WiFi networks, which can be used to determine the camera's location.

The creator made a video showcasing a unique musical instrument setup with 9 custom instruments, including NES timpani, using a combination of C64 hardware and clever audio processing. The video and audio were recorded simultaneously, with some sections recreated using an automaton for precise sound capture.
iRobot, a robotics company, filed for bankruptcy after being sold to a Chinese company, Shenzhen Picea Robotics, due to pressure from financiers on Wall Street. The deal was blocked by regulators, but the company's collapse highlights the consequences of prioritizing shareholder returns over innovation and national security.
FPGA development is limited by outdated proprietary software, hindering their full potential. Embracing open-source tools could modernize FPGA development and unlock their flexibility and efficiency.
The "block pattern" is a Rust idiom that organizes code into a block to improve readability and reduce namespace pollution by encapsulating implementation details. This pattern has several advantages, including clear intent, reduced pollution, and improved idiot-proofing, and can be used to restrict mutability and improve code flow.
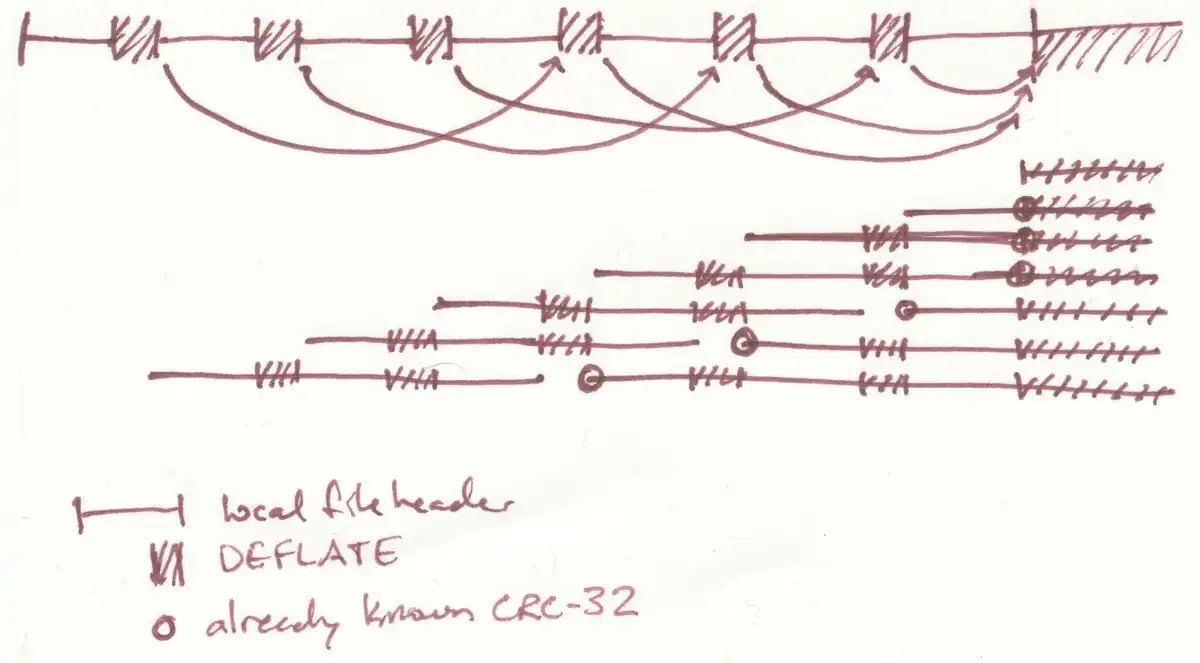
The user is trying to find information about the creator of 42.zip, a zip bomb that expands to 4.5 PB if recursively unzipped, and discusses its construction and optimization. The user also talks about optimizing the compression ratio of the zip bomb, using a custom DEFLATE compressor, and discusses the limits of the zip format and how to surpass them using Zip64.
A reconstructed source code for Commander Keen 1-3 has been released, allowing users to compile exact copies of the original executables using specific compilers and assemblers. The source code reveals that the IDLIB.C code was based on The Catacomb and Hovertank, and that the id founders likely used Softdisk's code in their own game without permission.
The document discusses general performance tuning principles and techniques for improving software performance, focusing on single-binary context and providing examples in C++ with illustrative source code changes. It emphasizes the importance of considering performance early on and using techniques such as algorithmic improvements, data structure optimization, and profiling tools to achieve ...
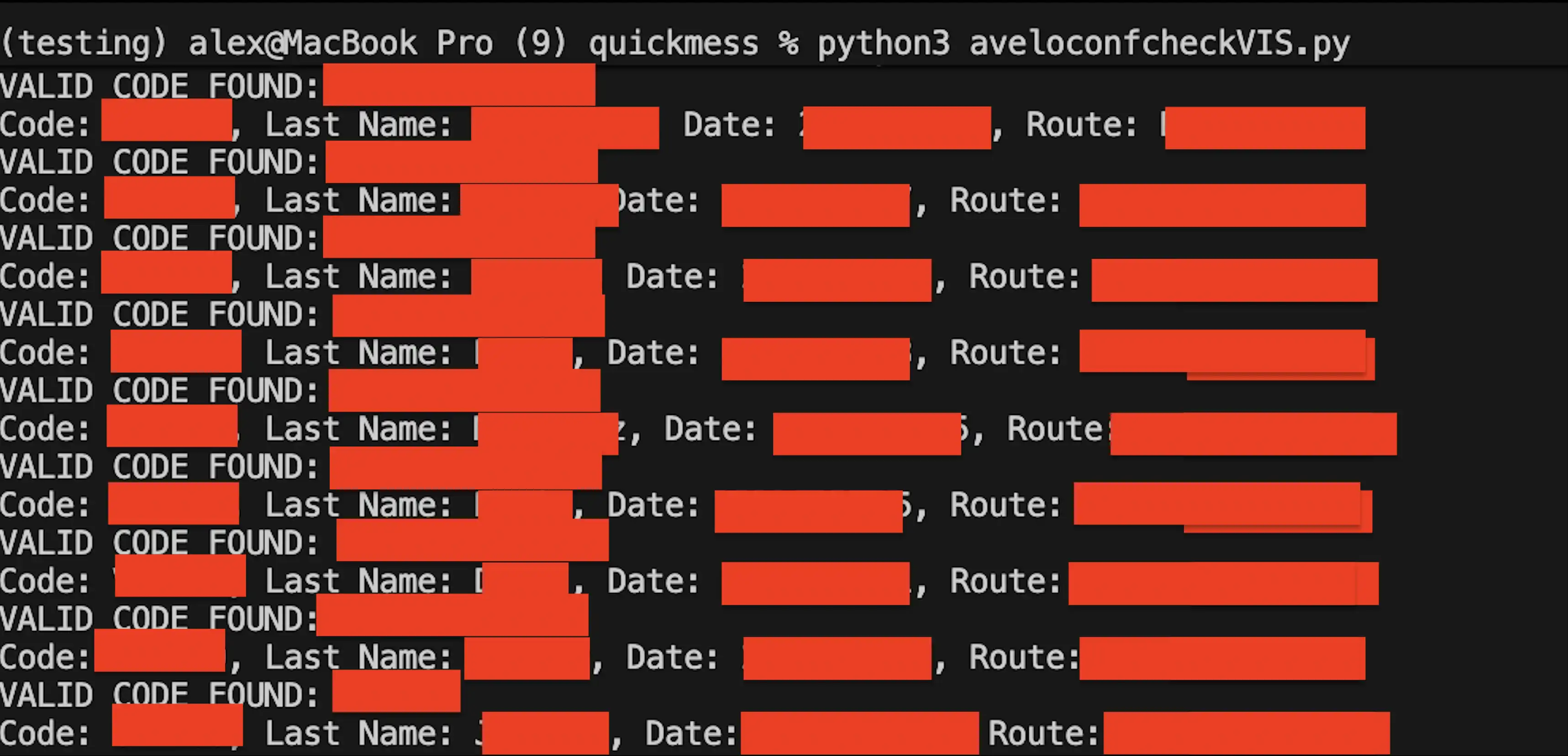
A vulnerability was discovered in Avelo Airlines' reservation system, allowing an attacker to access full reservation details, including PII, with a 6-character alphanumeric code and no last name verification. The Avelo team responded quickly and professionally, patched the issue, and maintained clear communication throughout the disclosure process.

The article discusses Kernighan's quote that debugging is twice as hard as writing code, but argues that this is not a reason to avoid clever techniques, as they can actually help improve skills through practice and motivation. The author suggests that writing code that respects the original idea and requires full capability can lead to bugs, but also to a point where the idea is honored and ...
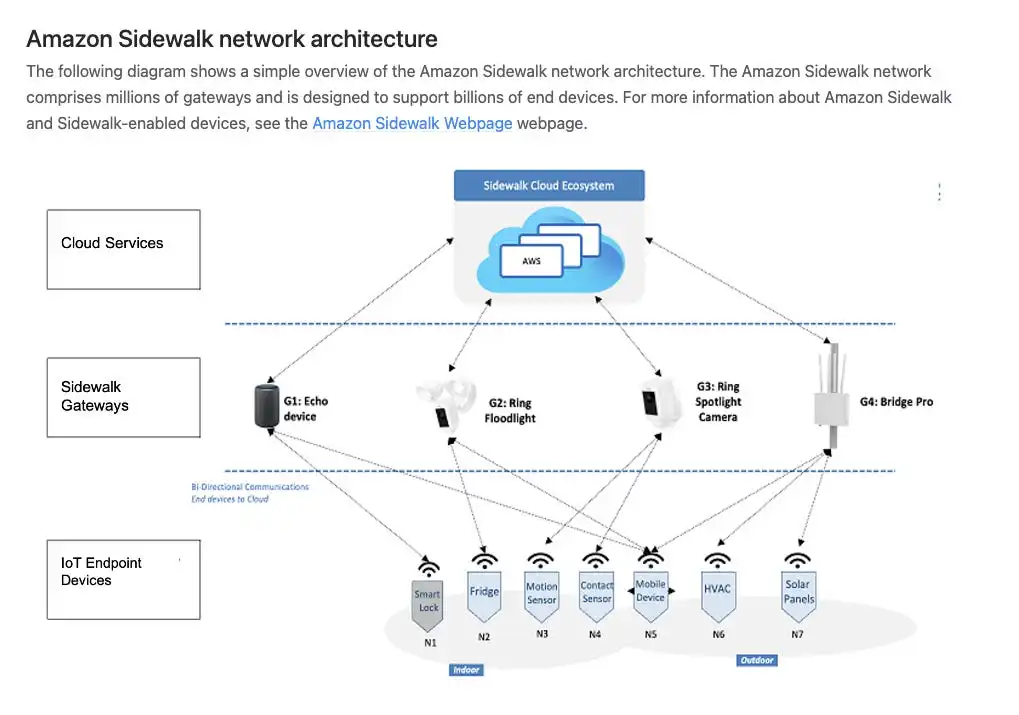
Netrinos creates a secure, private network that seamlessly bypasses firewalls and routers, giving you instant access to your devices from anywhere on the internet.No firewall changes. No port forwarding. No IT department. Encrypted tunnels protect your data while traversing networks, firewalls, and routers as if they don't exist.
People are using AI despite feeling conflicted about it, with 85.7% experiencing unresolved tensions. They're adopting AI for short-term benefits while worrying about long-term consequences.
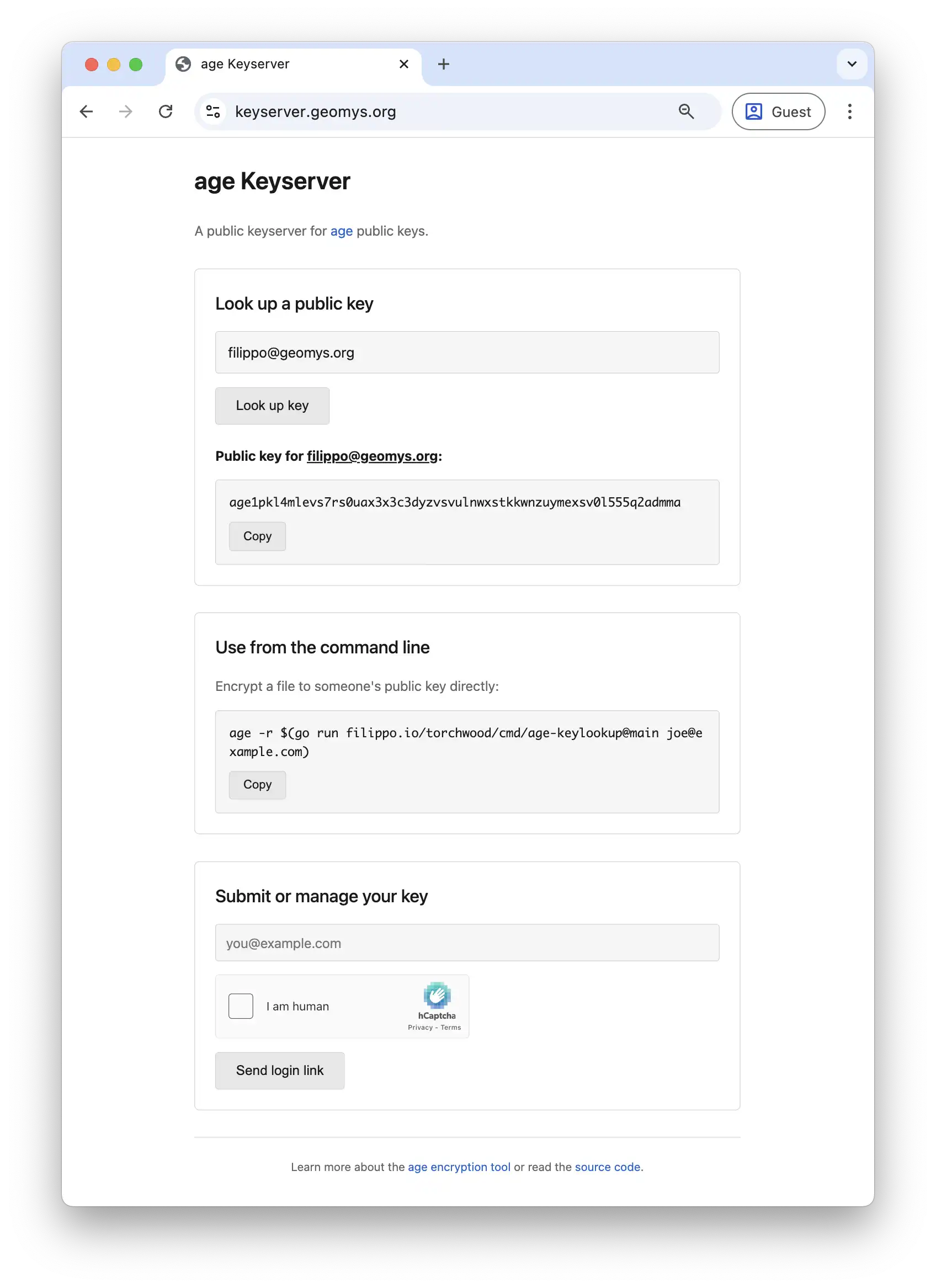
We built a keyserver that uses transparency log technology to keep the operator honest and protect user privacy, and we added features like Verifiable Random Functions and witness cosigners to prevent malicious activity. The keyserver now provides a secure and convenient way to fetch age public keys, and its transparency log can be monitored to ensure the operator is not serving unauthorized keys.
The author obtained an HP 9000/720 workstation and worked on porting OpenBSD to the PA-RISC architecture, with the help of Michael Shalayeff and later Matt Fredette who also ported NetBSD to the same architecture. The author eventually succeeded in allowing the OpenBSD boot blocks to display and modify the firmware's console path, enabling the 712 model to run with a serial console.

The user created a 3kB shoot 'em up game for a 7-day game jam using a custom bytecode VM and fullscreen pixel shader, combining interests in language tooling, game development, and demoscene-style size constraints. The game's design and bytecode were developed in parallel, allowing for rapid iteration and a fun project that worked better than expected, with the bytecode version being 90 bytes ...
The Buteyko method is a breathing technique that aims to regulate breathing and alleviate symptoms of asthma and other respiratory conditions by correcting hyperventilation and encouraging shallower breathing. Its effectiveness is disputed in the medical community due to limited evidence supporting its claims.
Demo Scope is a tool for mobile web content demos with face cam and touch indicators, supporting YouTube Live, Twitch, and custom RTMP servers. It offers a free version with limits and a one-time Pro purchase for unlimited use.
Researchers study chain-of-thought monitorability in AI systems and introduce a framework to evaluate it. They find that most frontier reasoning models are fairly monitorable, but monitorability can be fragile to changes in training procedure and scaling.

Tech publications in the Bay Area, such as Kernel and Palladium, reflect a shift in tech culture towards the right, promoting techno-optimism and militaristic nationalism. These publications serve as functional devices for class power, diffusing reactionary ideas into the common sense and influencing the tech world.
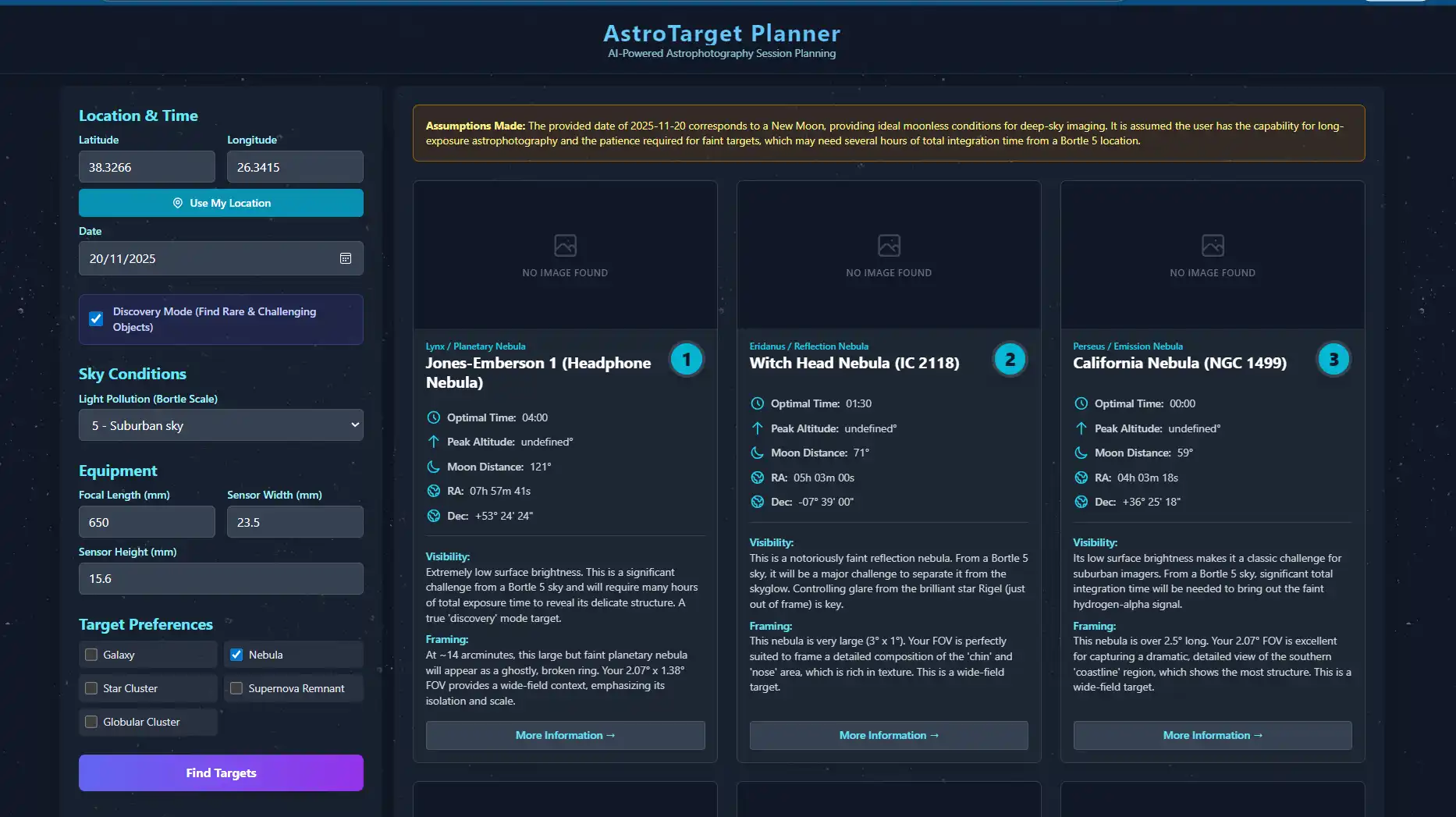
The user built an astrophotography target planner to discover new objects in the night sky, reducing repetition and increasing variety in their images. The planner app, called Astro Target, helps users find hidden gems like NGC 7822 and the Question Mark Nebula by filtering by location, visibility, and focal length.
The document discusses general performance tuning principles and techniques for improving software performance, focusing on single-binary context and providing examples in C++ with illustrative source code changes. It emphasizes the importance of considering performance early on and using techniques such as algorithmic improvements, data structure optimization, and profiling tools to achieve ...

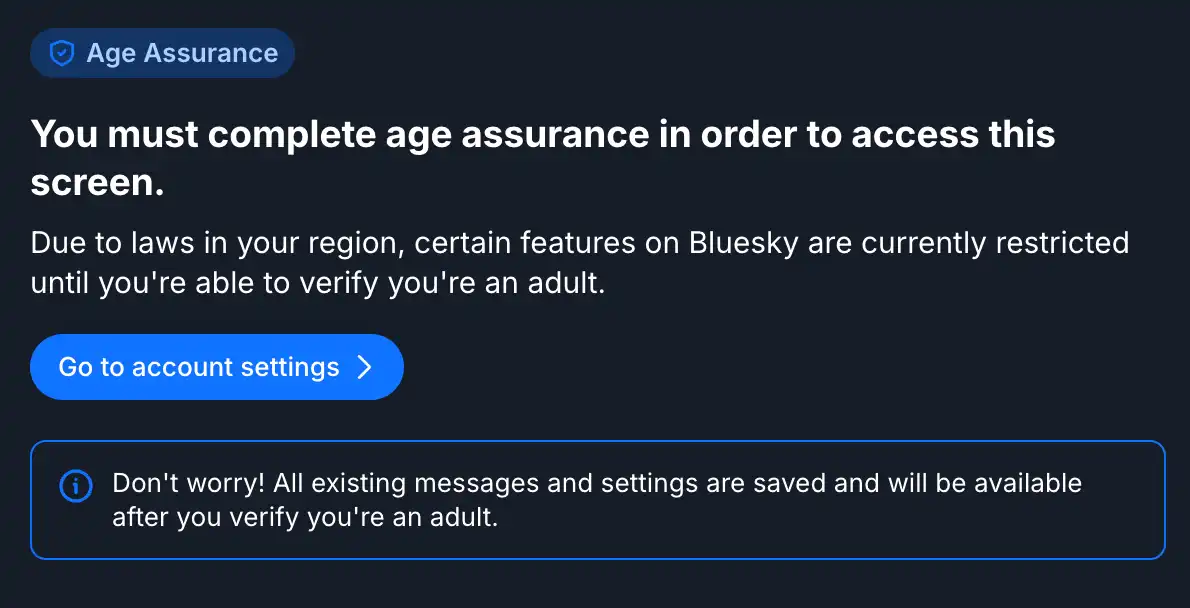
The UK's Online Safety Act 2023 amendment aims to prevent under 16s from accessing online services, but its scope is excessively broad, including self-hosted services and everyday online tools. This could lead to a "papers, please" approach, requiring age assurance for all users and significant privacy implications.
The author is working on a Java-based Emacs clone called Juicemacs, which aims to explore concurrency models and JIT compilation for Emacs Lisp, but faces challenges such as supporting various Emacs features and GUI capabilities. The author discusses the performance of Juicemacs compared to nativecomp, a JIT compiler in Emacs, and suggests that nativecomp has potential for improvement with ...

David Earn, a McMaster University professor, uncovered 50 years of Canadian infectious disease reports from 1939-1989, leading to a massive research project and a new database called CANDID. The database contains over a million disease incidence counts dating back to 1903, allowing researchers to study past outbreaks and prepare for future ones.
You use Automator to convert HEIC photos to JPG on your Mac, but prefer to use command line tools like imagemagick and exiftool on your Linux desktop.
Users are experiencing issues with YouTube including slow playback, freezing, and failure to load videos. Problems persist despite having stable internet connections and some users are paying for ad-free services.
Litex is a formal language based on set theory that offers a more natural way to express mathematical statements, making it easier for users to write and verify math, especially for those without hardcore mathematical training. Litex's design is more intuitive and easier to learn compared to Lean, a popular formal language based on type theory, but it is still a toy language for learning ...