The author sat alone in a café without distractions, enjoying time with their dog and observing people's lives. This experience showed them the beauty of slowing down and the futility of trying to control others' thoughts and feelings.
The user is watching a series of videos explaining neural networks and deep learning concepts such as backpropagation, Torch.Tensor, and language modeling. The videos cover topics like multilayer perceptrons, batch normalization, and generative pretrained transformers, and also delve into the importance of tokenization in large language models.
User runs 6 Claude Code agents in parallel from their phone using Termius and a cloud VM, enabling async development from anywhere. The setup includes Tailscale, mosh, and fail2ban for secure and seamless remote access and development.

Researchers at Stanford Medicine found a treatment that blocks a protein linked to aging, restoring cartilage in aging and injured joints by reprogramming existing cells. The treatment, which targets a protein called 15-PGDH, has shown promise in restoring cartilage in mice and human knee tissue, potentially eliminating the need for knee or hip replacement surgery.
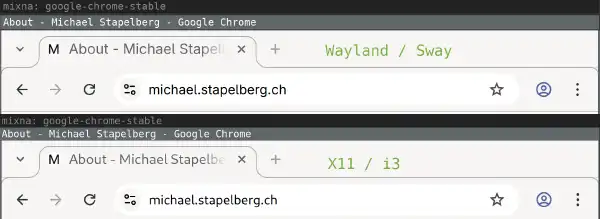
The user has been trying to switch to Wayland for 18 years but has been hindered by poor driver support, graphics glitches, and other issues, but has finally made progress with the latest nVidia driver and Sway 1.11. Despite this progress, the user still encounters many issues, including graphical glitches, input latency, and bugs, and will likely continue to use X11/i3 for now due to lack of ...
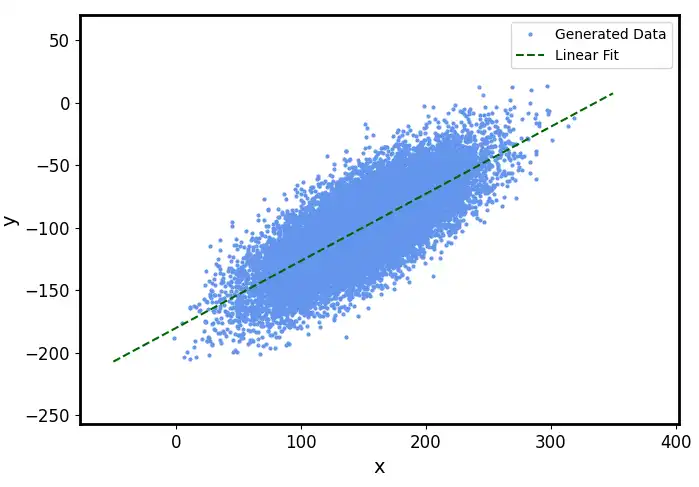
The user observed a biased linear least-squares fit in their data and found that the eigenvector with the maximum corresponding eigenvalue (PCA) gave a more expected result. This is due to the difference between ordinary least squares (OLS) and total least squares (TLS), where OLS treats the dependent and independent variables asymmetrically.
A guide to how browsers work is available, using interactive examples to help build an intuition of the technical details, omitting some critical details like HTTP protocol versions and DNS nuances. The guide explains how browsers transform URLs into HTTP requests, establish TCP connections, parse HTML, and render web pages using the DOM, CSS, and rendering pipeline.
She lived a long life, 95 years old, and then stabilized her appearance at 32. She used a headband to connect her mind with computers, which helped her in various ways, but also made her realize the Mountain was getting more dangerous due to climate change. She used the headband to see patterns of slippage in the ice and to spot crevasses from a distance. She became increasingly dependent on ...
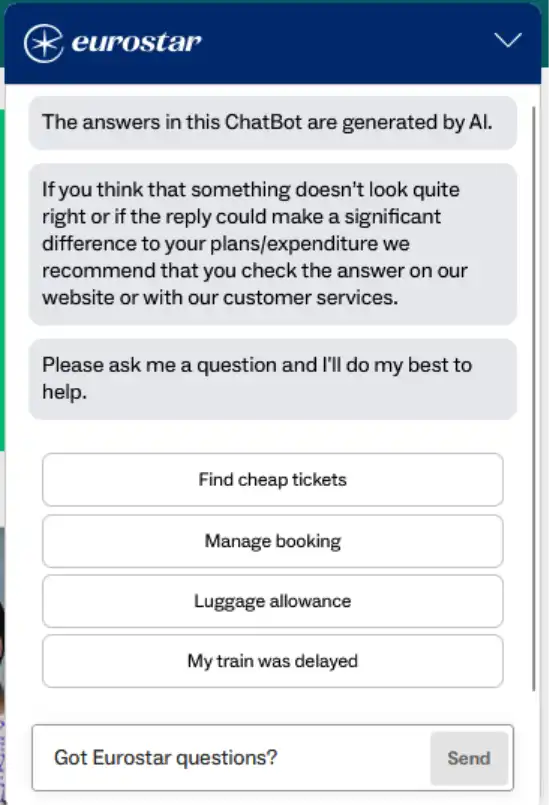
A security researcher found four issues in Eurostar's AI chatbot, including guardrail bypass and HTML injection, and disclosed them through the company's vulnerability disclosure programme. Despite initial silence, Eurostar eventually fixed some of the issues, but the researcher notes that the fixes are not exotic and should be applied consistently across the whole lifecycle of AI features.

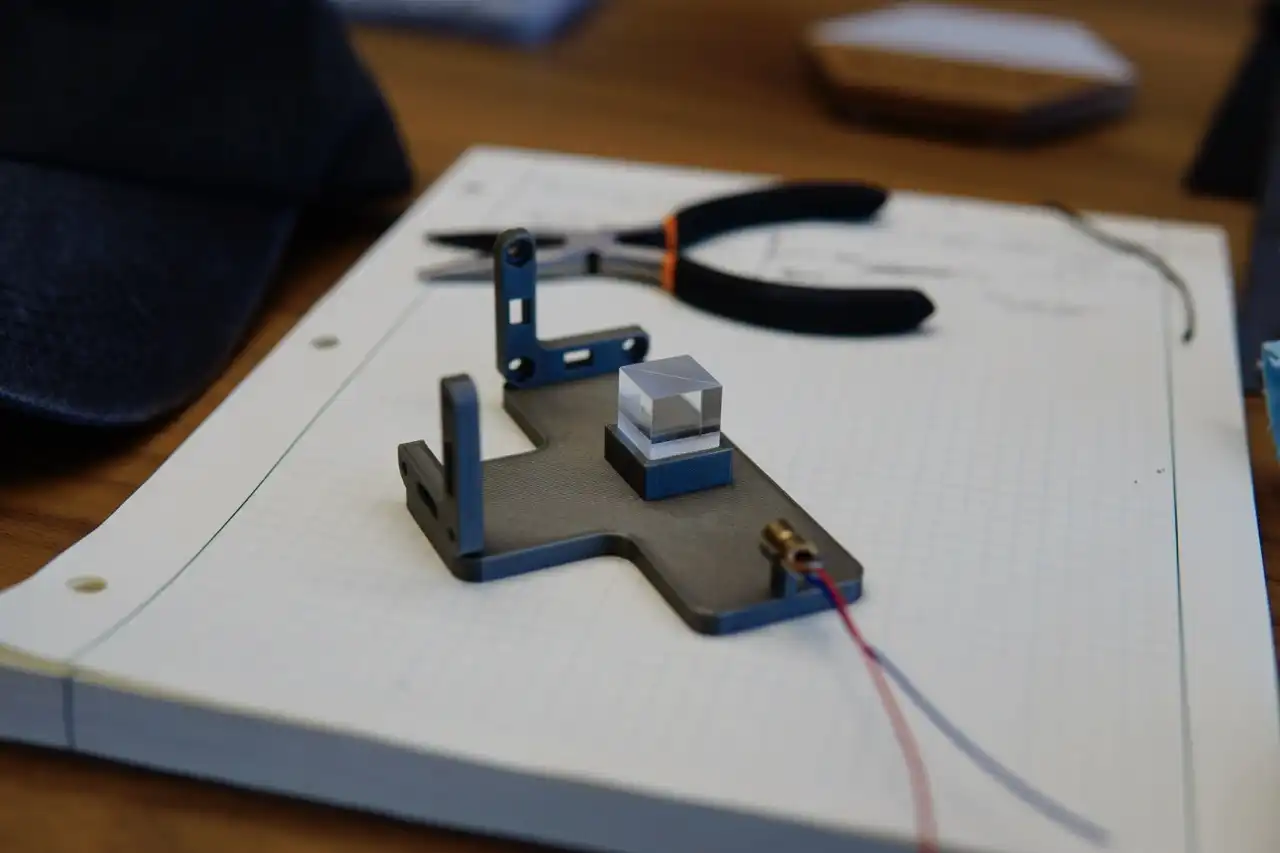
The user modified a CASIO F-91W watch to enable contactless payments by adding an NFC antenna and a microchip, using various tools and devices such as the NanoVNA and Proxmark3. The user successfully tested the modified watch and plans to add features such as security enhancements and a second coil, while emphasizing the importance of responsible usage and ethical considerations.
The author argues that comments should explain both 'what' and 'why' in code, as looking up information elsewhere can be frustrating and lead to assumptions. They propose that comments can be useful in certain cases, even if code is clean and descriptive.
The /bin vs /usr/bin split originated from a 1970s implementation detail on Unix, where the OS grew too big for a single disk pack. This split no longer makes sense and has been carried forward by bureaucrats without understanding its original purpose.
About/Manual L.S.D.
User contributed to KDE documentation, starting in 2021, and became its maintainer. They improved onboarding docs, fixed tutorials, and added content, making KDE's developer platform more accessible.
Request forbidden by administrative rules.

US rightwing podcaster Katie Miller posted a map of Greenland with the US flag and "SOON" caption after a US military operation in Venezuela, sparking outrage from Denmark. Denmark's ambassador to the US reminded the US of their defense ties and territorial integrity, amid concerns of a US takeover of the mineral-rich territory.

I am continuing to set up my home server on freebsd 14.3, which is intended to serve as a nas.... the result of what we’re about to do will look like this: the key is the routes. traffic goes through wg0, and the source address for the packet is set as 10.8.0.3. ping 192.168.0.165 (192.168.0.25) 56(84) bytes of data.
Something went wrong, but don’t fret — let’s give it another shot. Some privacy related extensions may cause issues on x.com. Please disable them and try again.
Something went wrong, but don’t fret — let’s give it another shot. Some privacy related extensions may cause issues on x.com. Please disable them and try again.
Click here if you are not redirected.
Error handling in software development is often flawed due to the focus on propagating errors exactly rather than providing meaningful context for debugging. A better approach involves categorizing errors by response and using context-tracking mechanisms to provide human-readable information for debugging and machine-readable data for automated recovery.

The user is exploring ways to incorporate the ancient Irish script Cló Gaelach into modern media, while preserving the original text for accessibility and data portability. They successfully used discretionary ligatures in a font to achieve the look of the old script and are now experimenting with repurposing HTML elements to preserve reading flow and screen reader functionality.
PGP is a flawed encryption system that has been outdated for decades and is no longer secure, yet many people still use it due to its complex and confusing nature. Instead of using PGP, users should consider alternative tools like Signal, Tarsnap, and age for secure messaging, backups, and file transfers.

The Great Gatsby's meaning has been misunderstood since its publication in 1925, with many readers focusing on its parties and glamour rather than its complex themes. The novel's enduring relevance is due to its exploration of the American Dream, class, and identity, which continues to resonate with readers today.
The engine uses a fixed virtual coordinate system of 800x600. All drawing commands (api.fill_rect, api.draw_line, etc.) use these coordinates. The engine automatically scales the output to fit the user's screen while maintaining the logical resolution and aspect ratio.
The professor shows a frozen baby painted turtle to demonstrate cold-blooded animals, which can adapt to temperature changes. This concept is applied to software projects, where cold-blooded projects use stable, low-maintenance technology to survive long periods of inactivity.
Please enable JS and disable any ad blocker
The author argues that the "Billion Dollar Mistake" of null pointer dereferences is not as big of a problem as people think, and that it's often caused by a specific mindset of thinking about individual elements rather than grouped elements. The author believes that this mindset is a necessary phase of thinking, but that it's inefficient and bug-prone, and that moving to a grouped-element ...
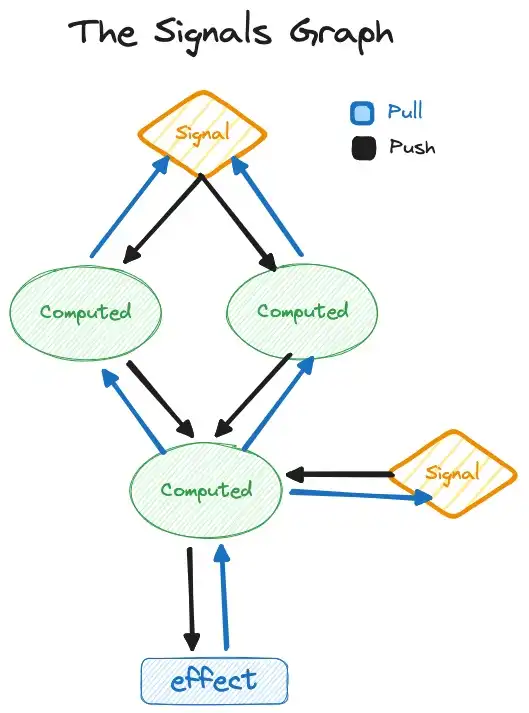
Query-based compilers have emerged as a new architecture, similar to Signals in UI rendering, but with different design choices, allowing for interactivity in the days of LSPs and tight editor integrations. This architecture is built around queries, inputs, and a database, with queries being pure functions over their inputs, allowing for caching and parallelization, and making it suitable for ...
Master SQL through hands-on practice. Write real SQL queries in our interactive playground with a social media database. Perfect for beginners learning SELECT, JOIN, INSERT, UPDATE, and more.
Skip to content You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session. Dismiss alert You can’t perform that action at this time.
A simple, powerful Bash script to batch download and organize YouTube playlists by channel name using yt-dlp. 1. Add your playlists: Edit playlists.txt and add your channels and playlist URLs in the format: 2. Cookies Place your cookies.txt file in the same directory. How do I pass cookies to yt-dlp?
Alexander Grothendieck described two math approaches: hammer and chisel (forceful) and softening liquid (gentle). The second approach, used by Grothendieck, involves understanding concepts deeply to lead to elegant computations.

The article explains how to train a neural network to play Tic-Tac-Toe using reinforcement learning in Jax, with a focus on pedagogy and simplicity. The training process involves using temporal difference learning, introducing a target network, and implementing epsilon-greedy sampling to balance exploration and exploitation.

The Millennium Challenge 2002 (MC '02) war game was scripted to ensure a US victory, but the red team led by Paul Van Riper surprised everyone by sinking 19 US ships. The exercise's shortcomings and unrealistic scenarios were later acknowledged, but senior Pentagon officials were unwilling to hear the bad news.
The AIE array is a 2D grid of tiles that can be connected to neighboring tiles, and the aiecompiler compiles AIE programs to a design that can run on the AIE array. The AIE array can be used to implement BLAS routines such as scal, dot, and gemv, and the performance of these routines can be improved using techniques such as tiling and dataflow.
MOVE TO EXPLORE
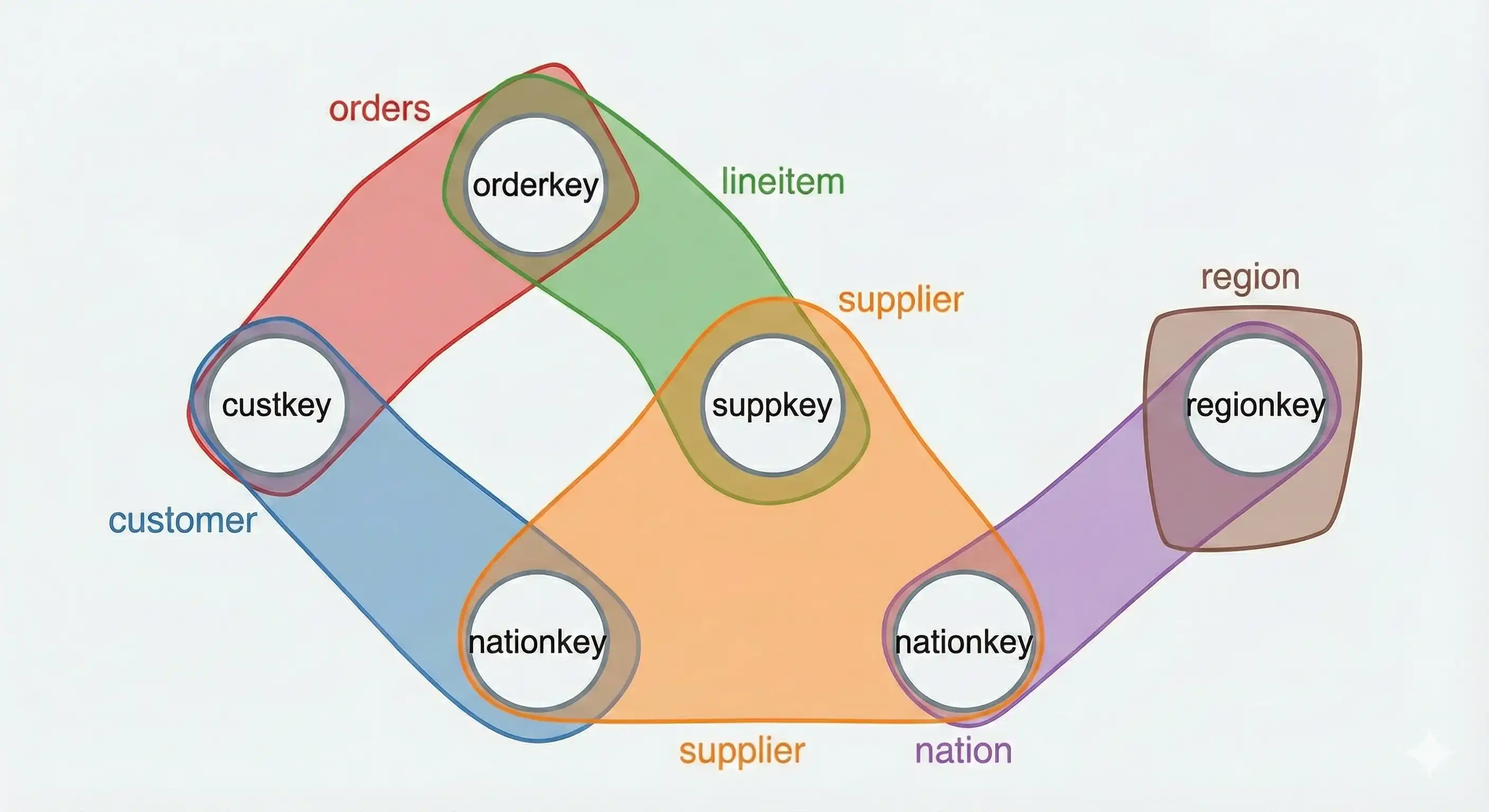
The join problem can be represented as a graph where nodes are join variables and edges are relations, and results from graph theory can be applied to joins, such as vertex cover and edge cover, to establish bounds on the output size of a query. The AGM bound, a relaxed version of the edge cover, provides a valid bound on the output size of a query, and can be used to determine the worst-case ...

María Corina Machado, a Venezuelan opposition leader, was extracted from Venezuela by US Special Forces Veteran Bryan Stern and his team, Grey Bull Rescue Foundation. They successfully navigated a treacherous sea route to a Caribbean island, where Machado boarded a private plane to Oslo for the Nobel Peace Prize ceremony.
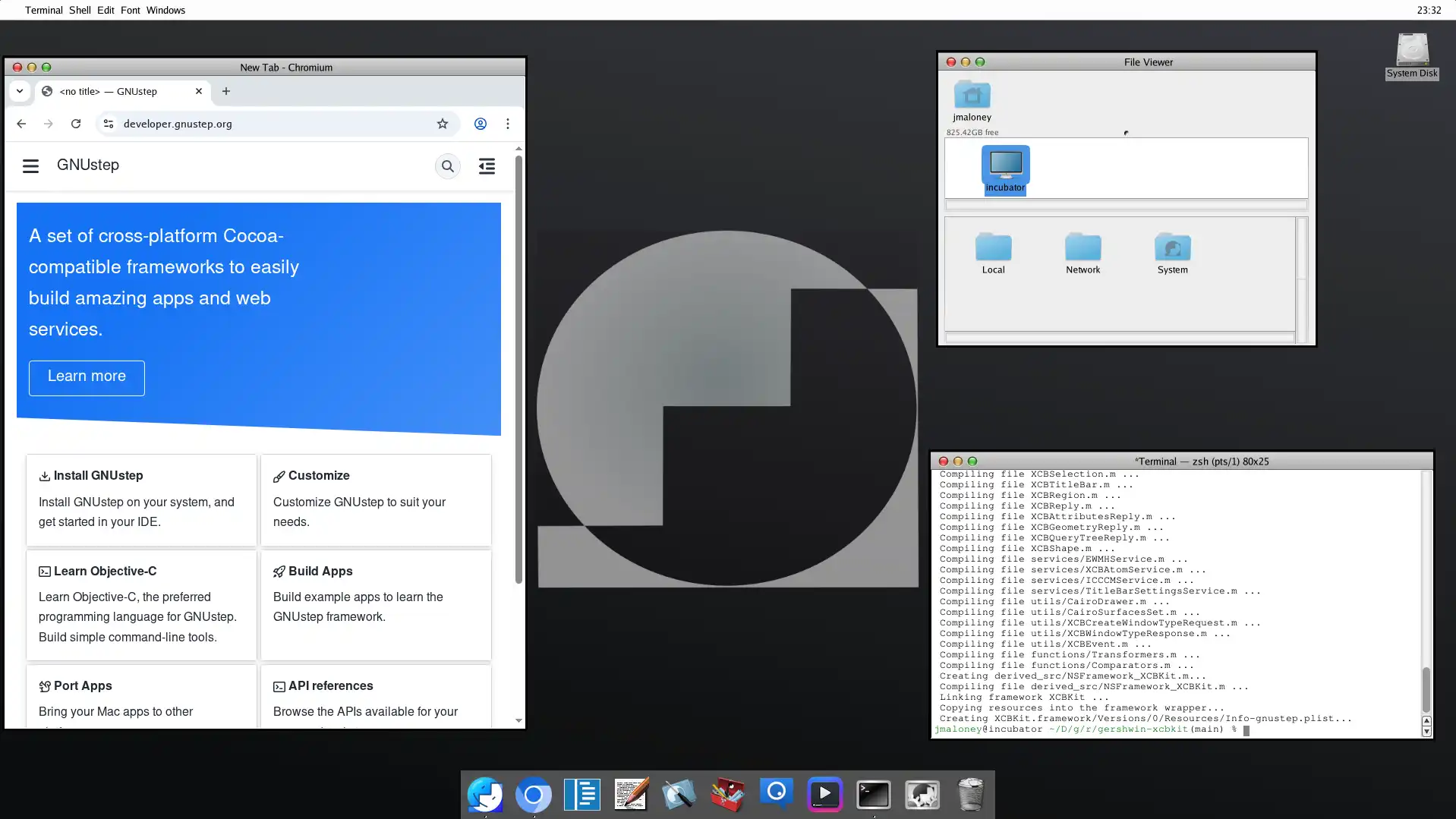
This project involves integrating Swift with GNUStep's Objective-C runtime, requiring the installation of GNUStep Desktop and Swift 5.8.1 on Debian, and implementing a Swift library to wrap GNUStep's GUI library. The project also involves creating a GNUStepNSObjectWrapper class to manage Objective-C objects and implementing functions to send messages and manage memory, with the goal of making ...

Democracy has become a system where the consuming majority extracts wealth from the productive minority, leading to a decline in the productive base and eventual collapse. To reform this system, incentives need to be rebalanced to favor production over consumption, and a cultural shift is needed to honor makers over takers.
An interactive WebGL visualization of the Seed of Life sacred geometry pattern with dynamic twisting, chromatic aberration, and customizable parameters.
Uruguay's young people fled poverty and violence in the 20th century, while Latin America suffered under colonialism and imperialism, leading to exploitation and underdevelopment. The region's history is marked by foreign domination, forced labor, and economic inequality, with the US playing a significant role in shaping its destiny.
The Commodore 64's BASIC interpreter can be hijacked to load and run programs automatically by exploiting a 89-byte region of unused memory and overriding the BASIC warm start vector. A loader program can be created to load and run programs by using system calls and manipulating memory, but requires careful attention to space constraints and potential issues with the BASIC interpreter's state.