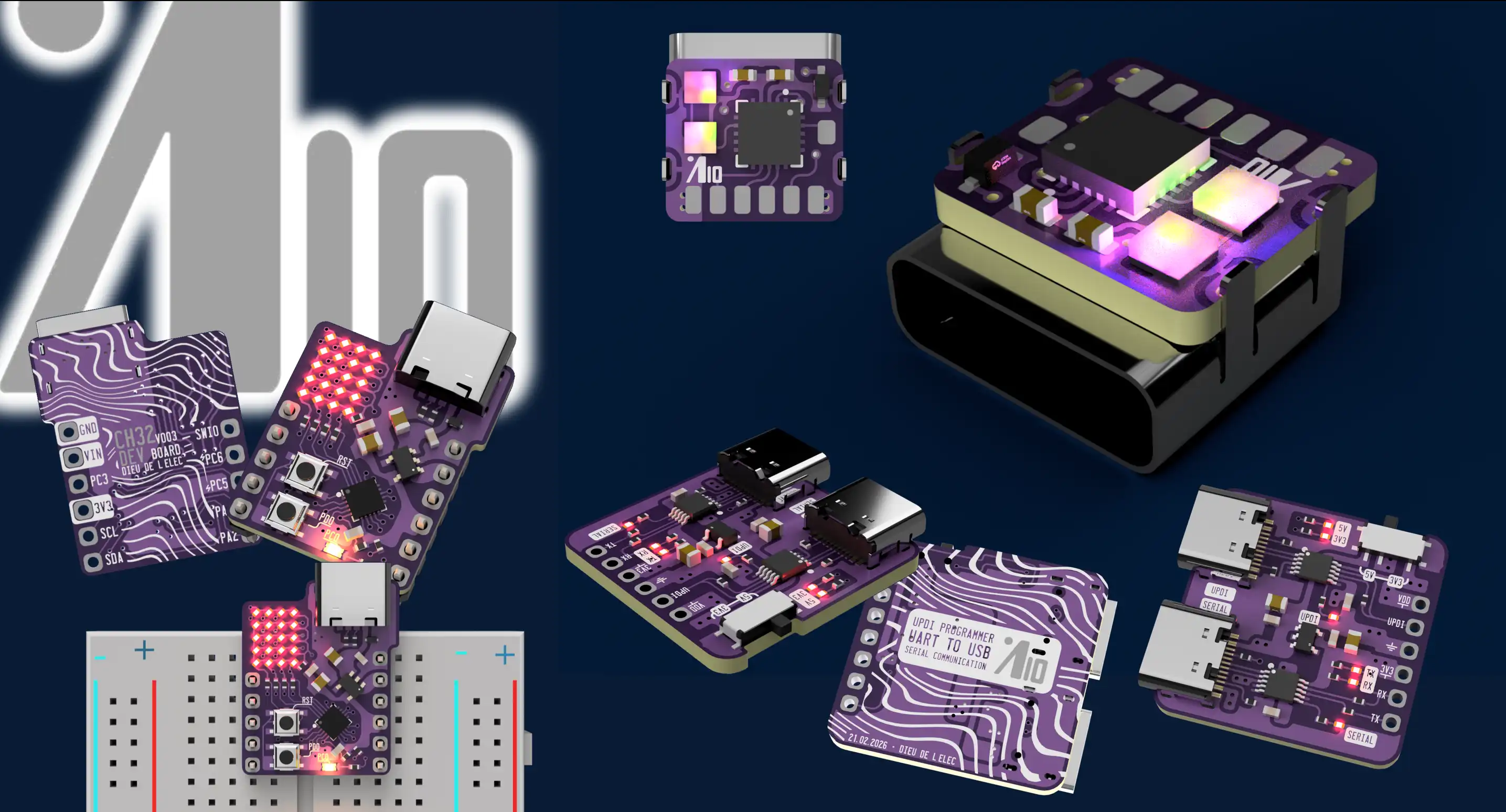
Literate programming, where code is intermingled with prose, can be cumbersome to maintain but is made practical with the help of coding agents that can keep the prose in sync with code changes. With agents, large codebases can be read like a narrative, improving code quality and making it easier to export code into various formats for comfortable reading.
The user discussed various projects including a deferred deep linking service, an Agent Registry for Docker containers, and a Rust alternative to icloudpd for downloading iCloud Photos. They also mentioned several other projects such as an open platform for independent music communities, a free in-browser inbox for inspecting email files, and a tool for collecting written testimonials from clients.

The user retrofitted a first-gen MacBook with new guts, including an M1 Mini, and created a custom case using 3D printing and old OEM parts. The project took three months to complete and taught the user various skills, including soldering and 3D modeling, despite some challenges and areas for improvement.
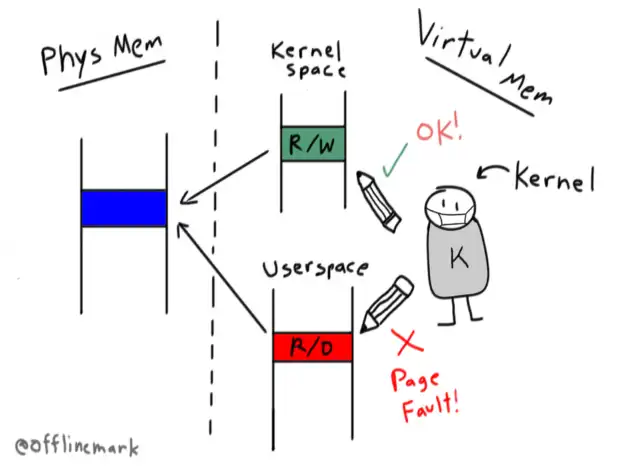
The Linux kernel's /proc/*/mem pseudofile allows writes to unwritable memory pages due to its "punch through" semantics, which are used by projects like the Julia JIT compiler and rr debugger. The kernel bypasses CPU settings like CR0.WP and SMAP to achieve this by manually mapping physical frames into its own virtual address space and performing writes using a simple memcpy.
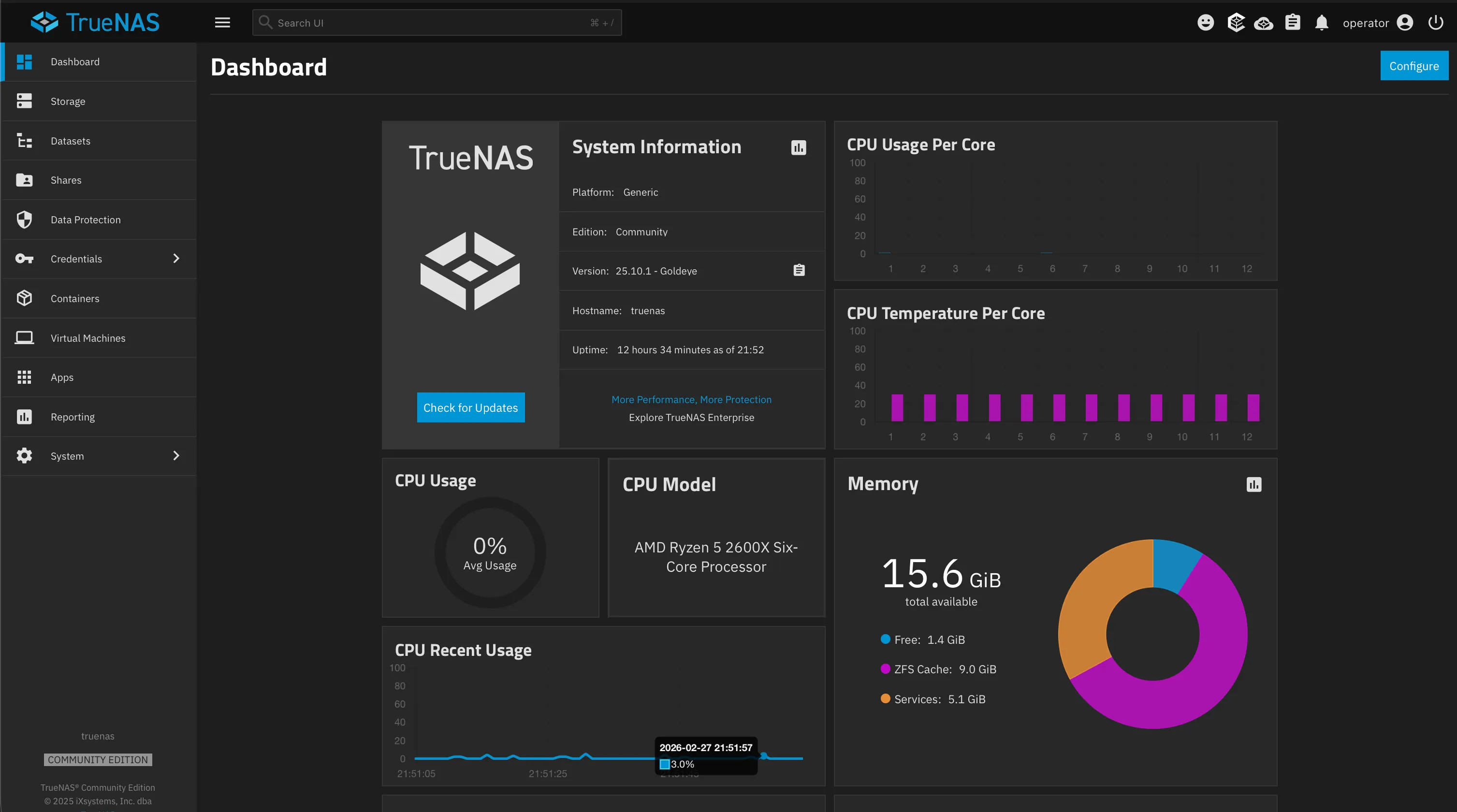
The user set up a homelab using an old gaming PC to meet storage and backup needs, installing TrueNAS for file storage and self-hosting various apps including photo management, recipe management, and AI model running. They also set up a VPN service to access their data and self-hosted apps remotely from any device, but plan to assign custom domain names to each service for easier access.
Social media was once hailed as the great democratizer of information. It promised a world where anyone could share their voice, connect with like-minded communities, and discover authentic human perspectives. But in 2025, the landscape looks very different. Social platforms are drowning in a flood of Generative AI (GenAI) content—articles, images, videos, and even entire conversations ...

The author created a programming language called MNM Lang where code is represented by colored candies, with each color corresponding to a specific instruction or operation, and a photo decoder can recover programs from images of the candy layout. The project involved designing a compiler, interpreter, and runtime environment, as well as testing and debugging the system to ensure it was ...
You're preparing to build a reactive engine for work and are considering three ways to build it: push reactivity, pull reactivity, and a hybrid push-pull combination. Each approach has its advantages and disadvantages, with push-pull reactivity being a hybrid approach that combines the benefits of both push and pull reactivity to achieve efficiency, fine-grained updates, and glitchlessness.
Skir is a declarative language for defining data types and APIs, generating idiomatic code in various languages. It provides a simple workflow for evolving schemas and exchanging data between frontend and backend.
A font is created to convert hexadecimal characters into disassembled Z80 instructions using OpenType's Glyph Substitution Table and Glyph Positioning Table. The font's implementation involves a recursive descent parser, contextual chaining rules, and lookaheads to handle various instruction combinations and out-of-order operands.
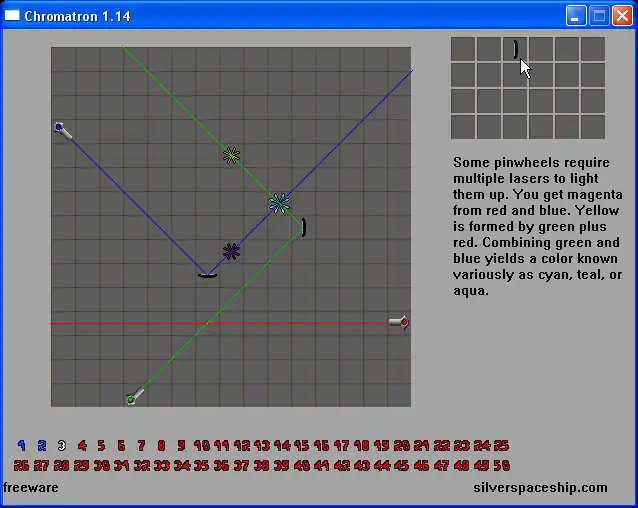
I recompiled an old game from WinXP and PowerPC binaries to Apple Silicon and WASM. And you can too! A colleague used Ghidra to add infinite lives in River Raid, a classic Atari game. I got inspired to give this open-source decompiler by the NSA a try. Flipping one assembly instruction is one thing. But recovering an entire game is another. I wanted to start with something small, so there ...
A 38-year-old man is struggling to adjust to being alone after a long-term relationship ended. He finds it hard to fill his time and feels hollow without social interaction.
The speaker is apologizing to the families of the victims and expressing remorse for their actions. They are also thanking their loved ones, spiritual advisors, and the administration for their support and kindness.
The user explores an alternate history where the field-sequential color system was adopted instead of composite video, and imagines what an early mass-market 8-bit computer, the Columbia ][, would have looked like in this world. The user details the technical specifications and limitations of the Columbia ][, including its resolution, pixel clock, and color palette, and discusses the ...
User concerned about AI generated posts on HN, wants restrictions or filtering options to reduce noise. Fears HN becoming like Twitter with bots and noise.